Advanced Networking and Security
Introduction
With the security audit underway, our VM-based application architecture is becoming more distributed, spanning multiple namespaces, projects, and even different cloud environments. Our VMs and new containerized services need to communicate seamlessly, and we need clear visibility and precise control over network traffic, especially as managing both virtual machines (VMs) and containers increases complexity in ensuring efficient and secure operations. In this section we will learn more about visualizing network traffic flows the the Network Observability Operator, and how to shape and secure our network by implementing Network Policies.
Configure Network Policies to Manage VM Traffic
In Red Hat OpenShift administrators can configure Network Policies to further secure their environments, and the virtual guests that run there.
In this portion of the lab we are going to configure a virtual machine and then apply a network policy that prevents its egress to the world.
Configure Network Policies to Manage Cluster Egress
In some secure environments network traffic is not allowed to leave the cluster without first passing through a proxy or some other secure gateway. Likewise, many network configurations allow for cluster egress by default. In this section of the lab we will be configuring a network policy that secures our cluster by blocking egress to outside websites.
Confirm Network Egress on Virtual Machines
-
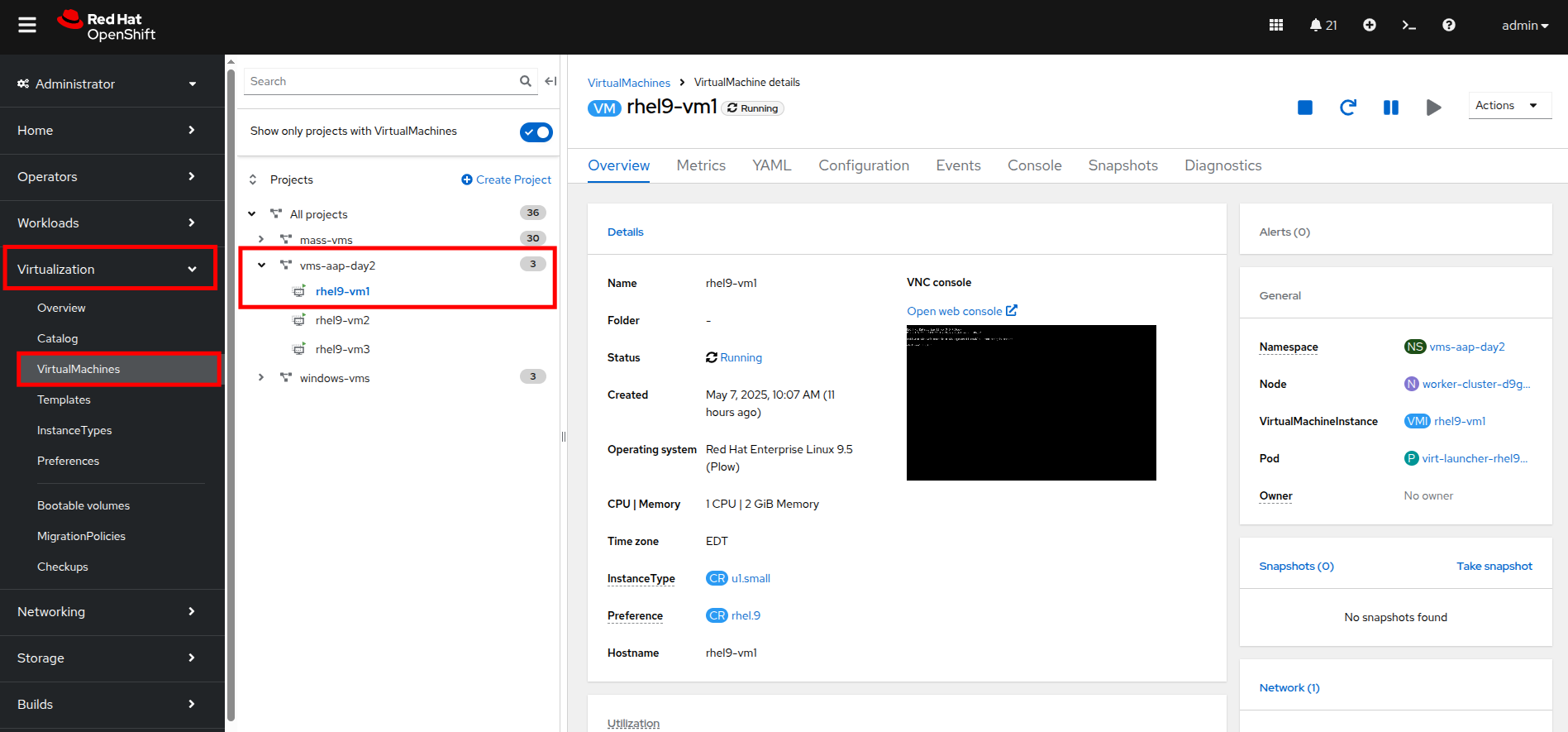
On the left side navigation menu, click on Virtualization then click VirtualMachines, and select the rhel9-vm1 virtual machine under the vms-aap-day2 project in the center column.
-
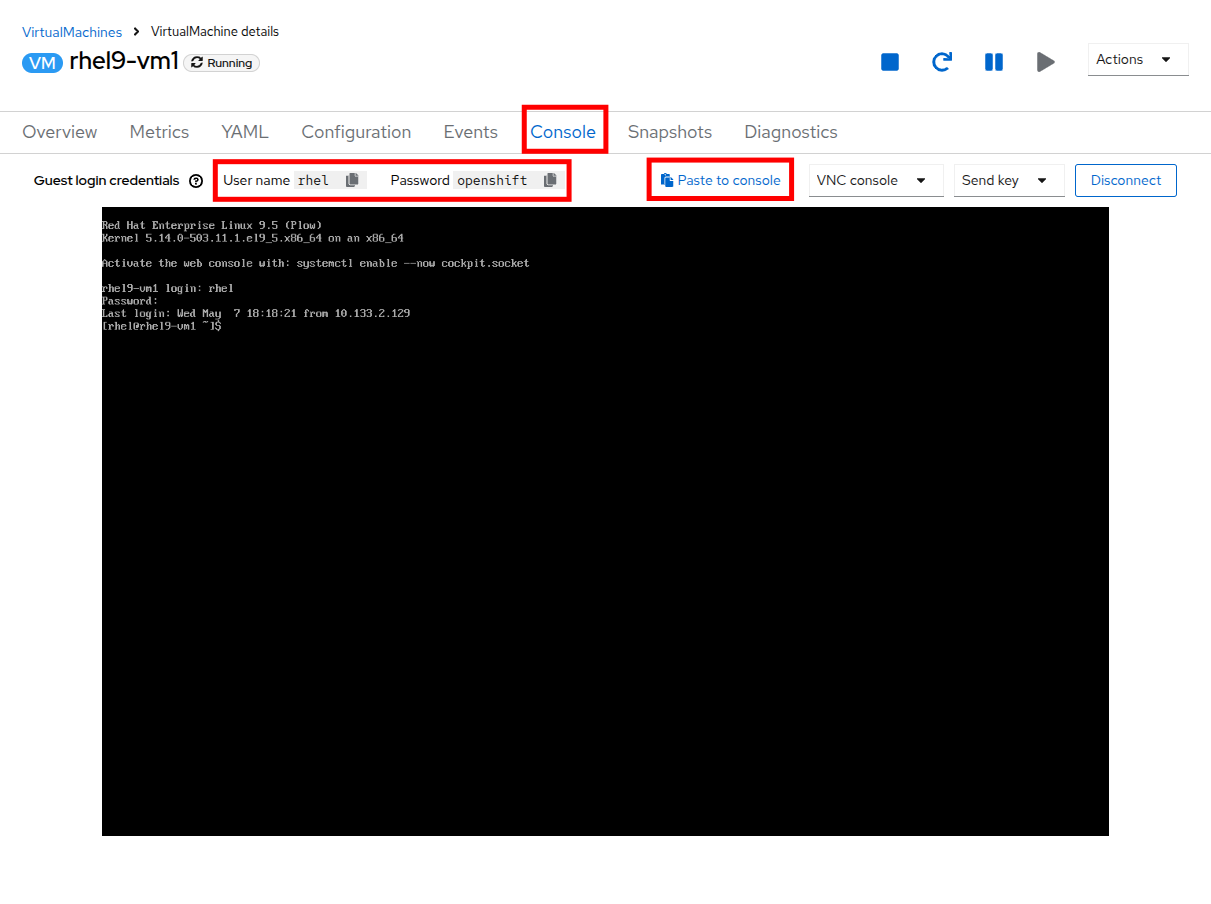
Click on the Console tab and use the provided credentials, and the built in copy/paste functionality to authenticate to the VM.
You may see a popup that asks you to enable the copy/paste functionality. If prompted click Allow. -
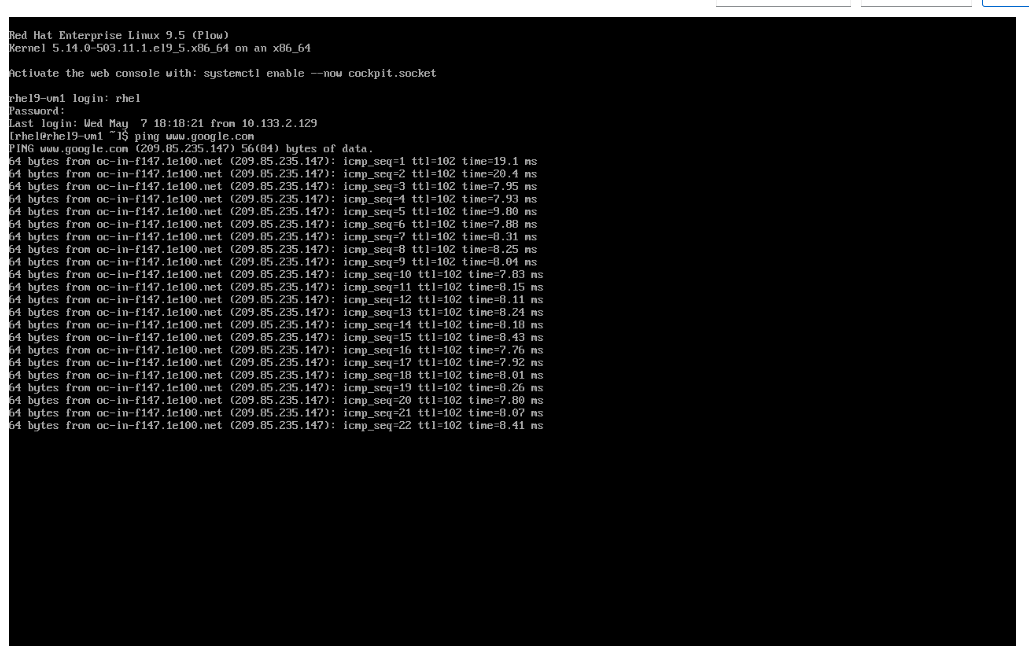
Once you are logged in, execute the following command to start an outward bound ping to Google:
ping www.google.com -
Press Control+C to stop the ping.
-
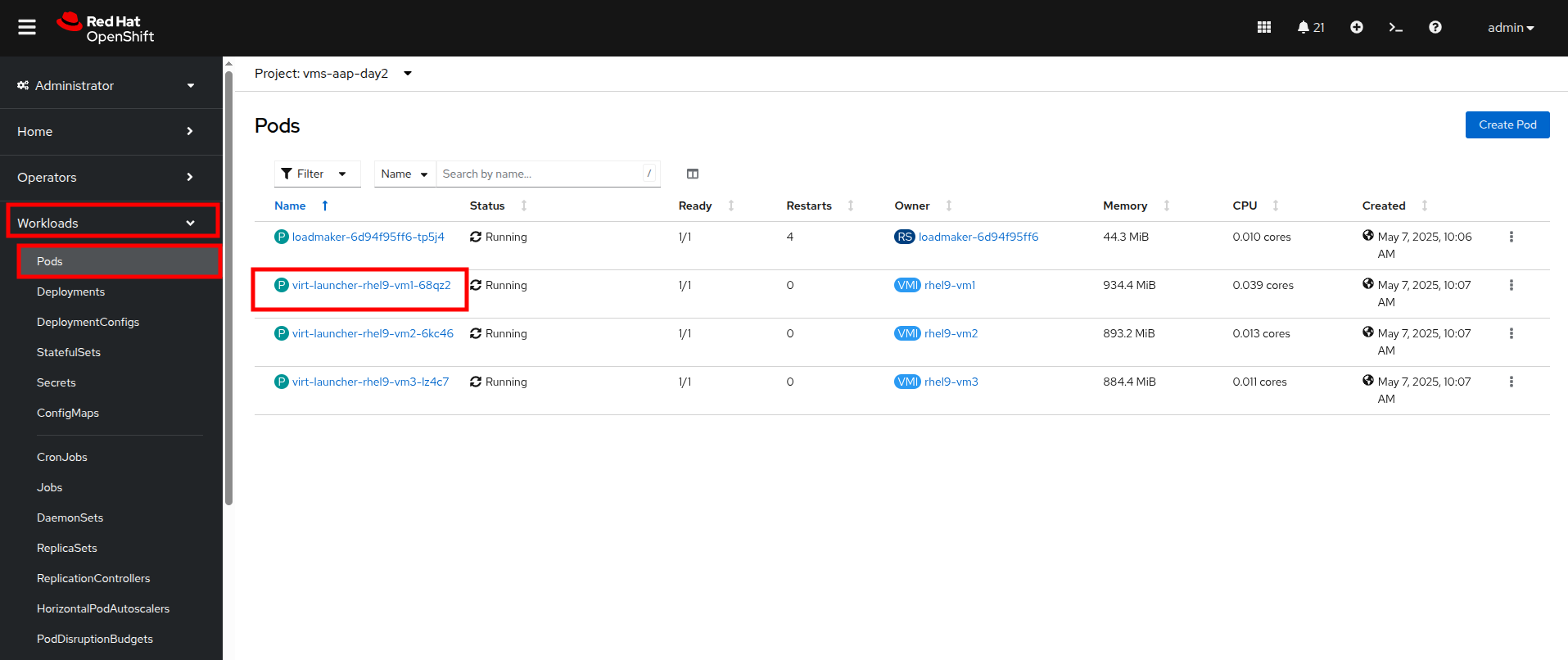
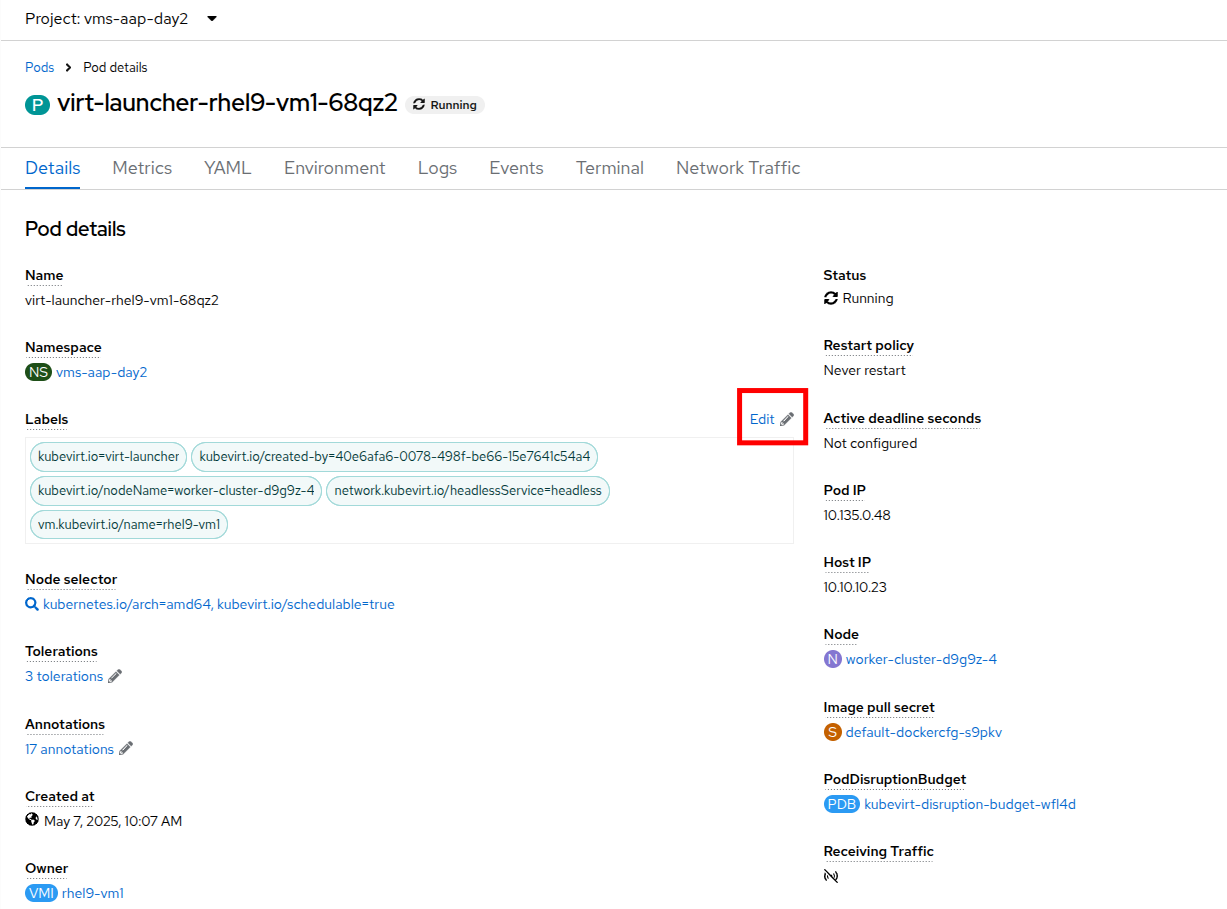
From the left side navigation menu, click on Workloads and then Pods, and then click on the virt-launcher pod for the one that represents the VM rhel9-vm1 to view the pod details.
Pod names are randomly generated, so yours will most likely not match the screenshot above. -
On the Pod details page, click the Edit option on the Labels section.
-
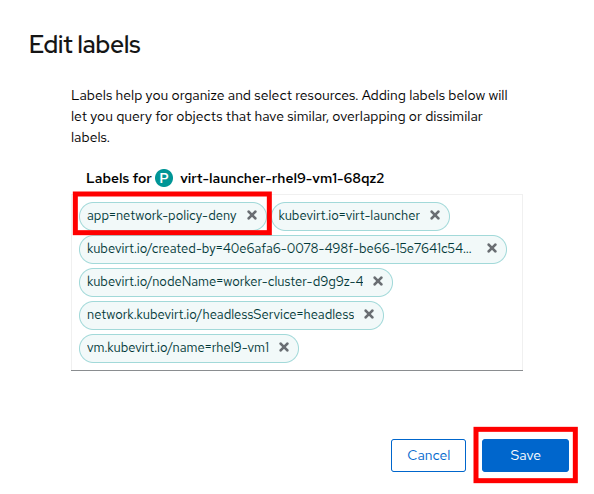
An Edit labels window will appear, you can click into the center box and add a label for
app=network-policy-deny, press the Enter key to commit it, and then click the Save button. -
Repeat the same process for the rhel9-vm2 virtual machine.
Create the Network Policy
-
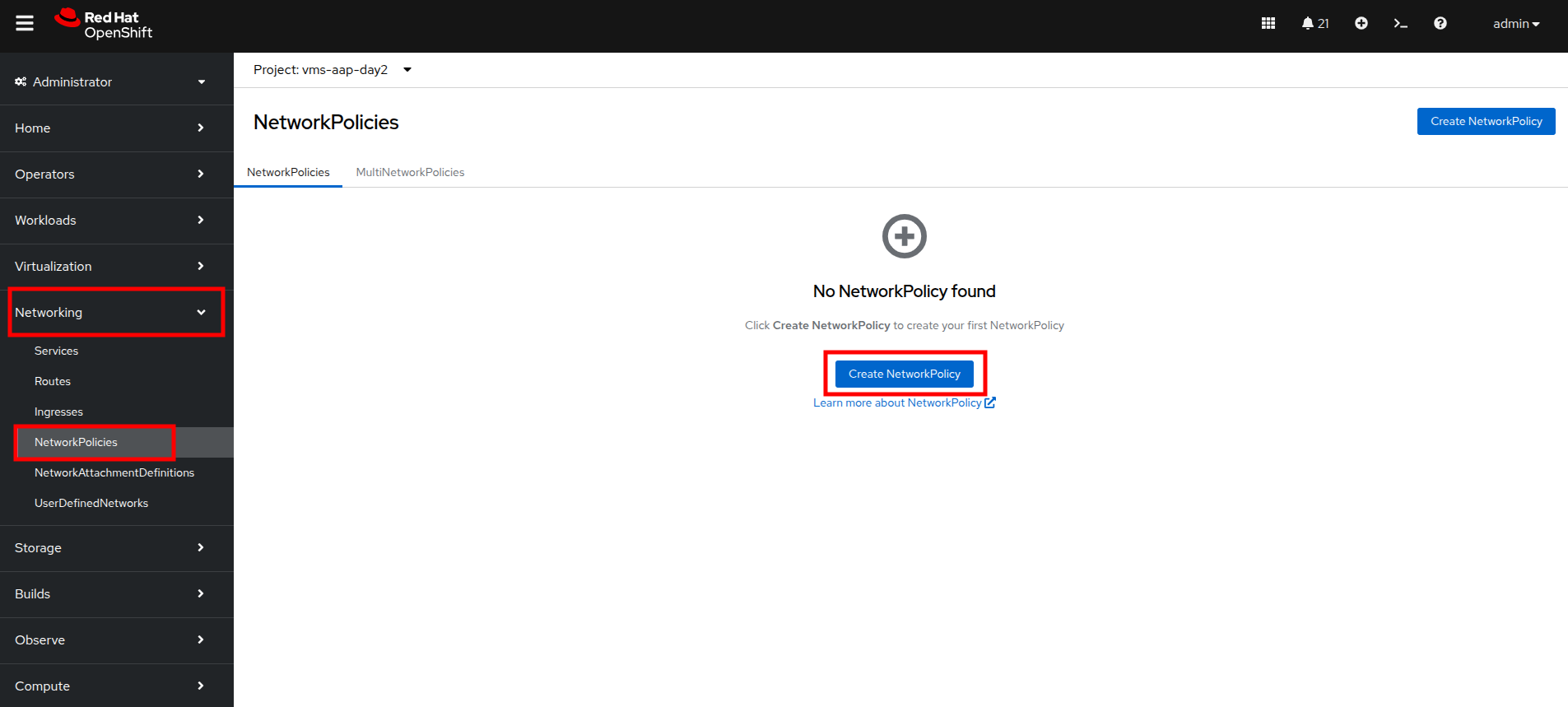
From the left side navigation menu, click on Networking and then click on NetworkPolicies, then click on the Create NetworkPolicy button in the center of the screen.
-
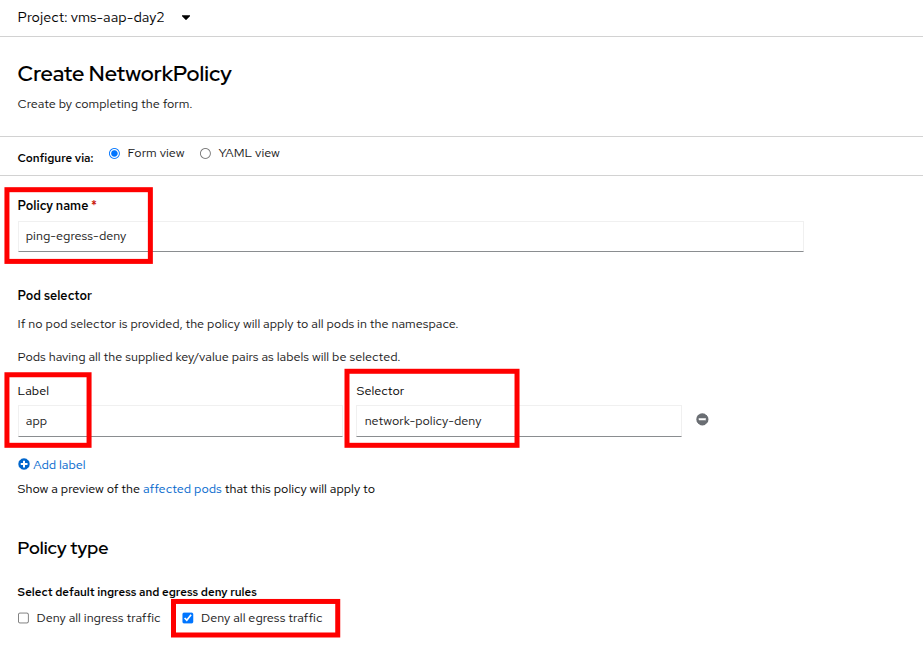
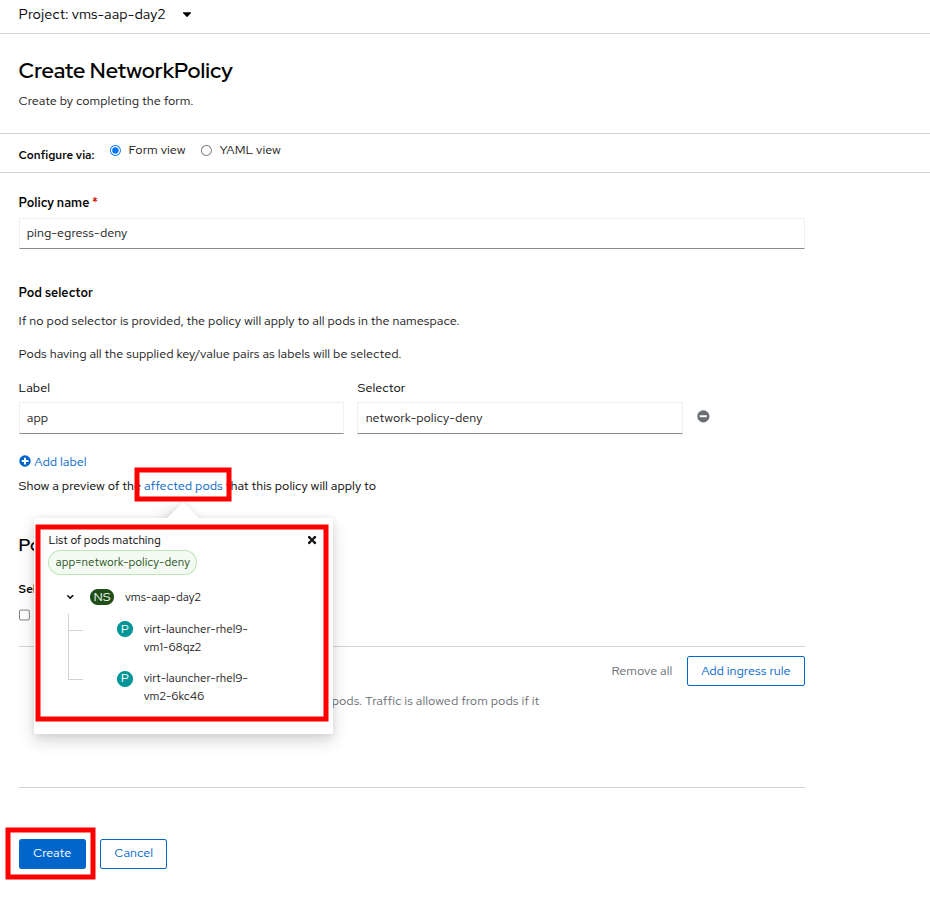
In NetworkPolicies fill out the following fields:
-
With the values filled out, you can click the affected pods link under the Pod selector section to show which pods are affected by this policy. Once you are satisfied with your settings you can click the Create button.
-
With the policy created, go test it out.
Confirm the Effects of the Network Policy on the VM.
-
Return to the console of the rhel9-vm1 virtual machine to test our policy.
-
Using the left side navigation menu, click on Virtualization, then VirtualMachines, and select rhel9-vm1 from the center column.
-
Click the Console tab of the VM, you should still be logged in from before.
-
Copy and paste the following syntax to test out the new Network Policy:
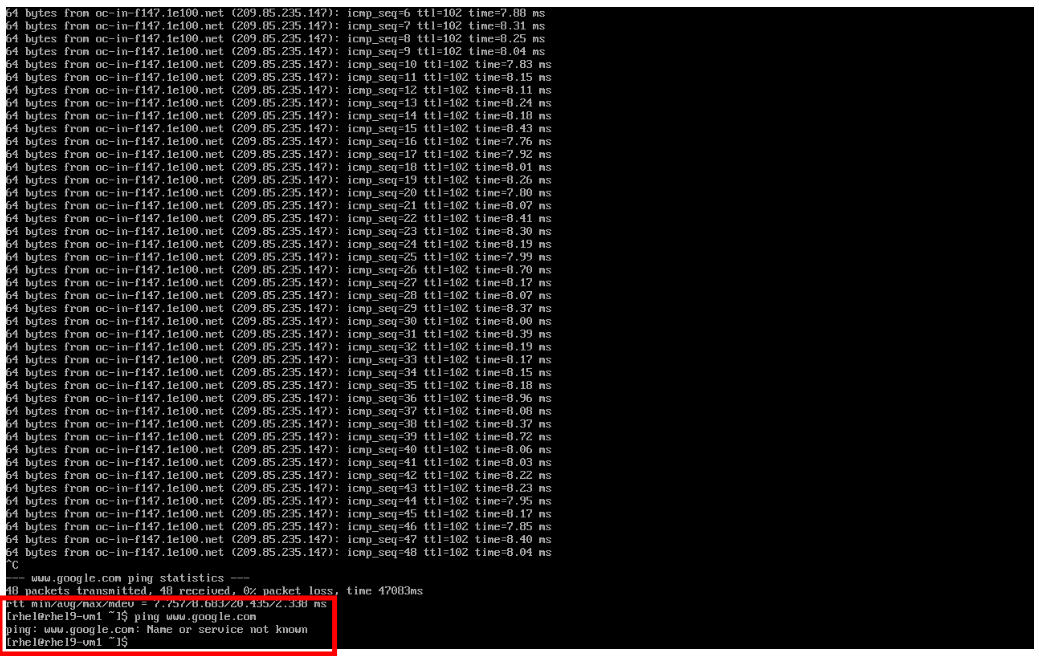
ping www.google.com -
Egress from the cluster is completely blocked, including DNS lookups.
-
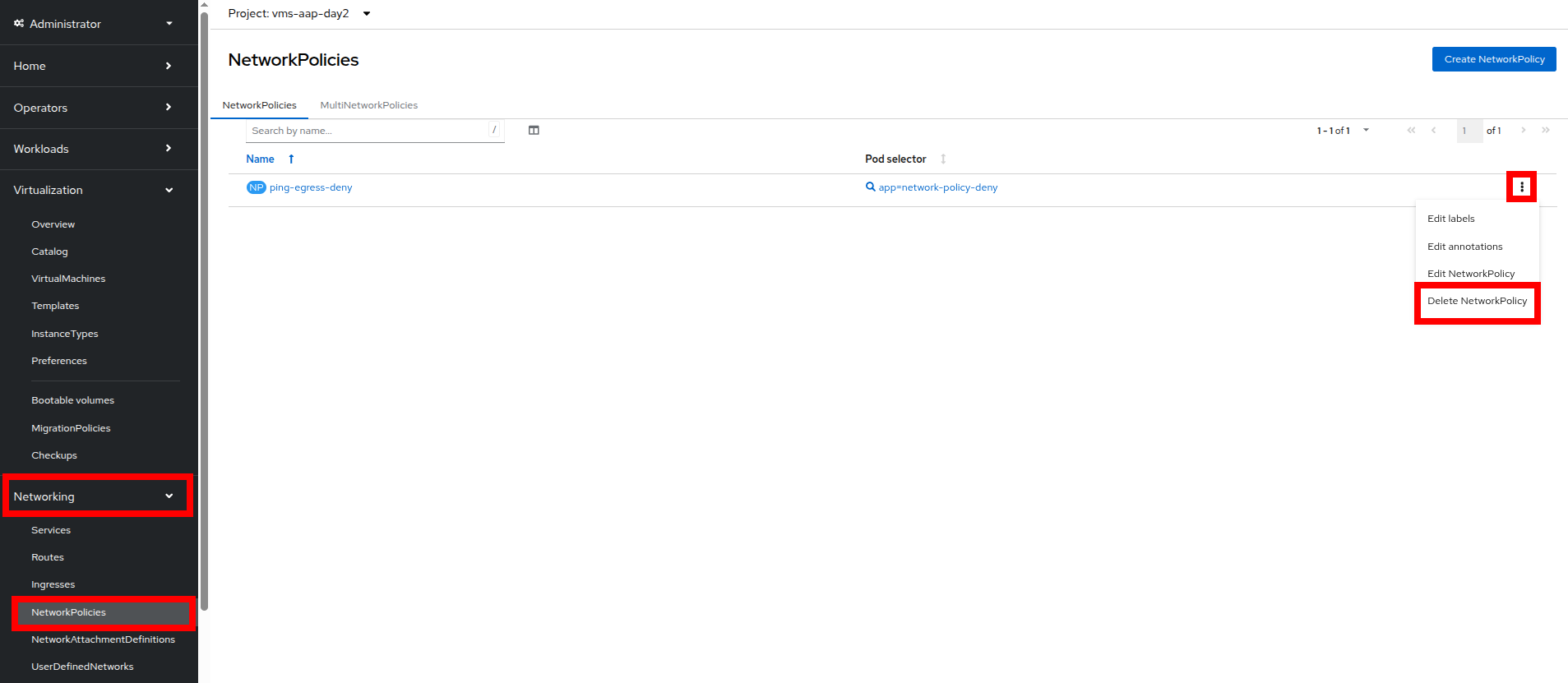
Once you have completed this exercise, return to Networking and NetworkPolicies and delete the ping-egress-deny policy using the three-dot menu on the right, and confirming in the popup box.
Summary
In this section we learned how to make use of the Network Observability Operator to scan our cluster and visualize traffic patterns in and out. We then learned how to create and apply a simple network policy to block egress traffic from a virtual machine to a public website, and as an advanced example we learned to shape traffic between virtual guests and projects on the same cluster. Overall Network Policies are quite robust, and allow you to implement microsegmentation policies helping to shape the traffic flow both inside and outside of your cluster, between virtual guests in different or even the same OpenShift project.