Jenkins Pipelines - Production
- Learning Objectives
- Understanding Jenkins Production Transformation
- Activity 1: Understanding Jenkins Production Triggers
- Activity 2: Creating a GitLab Release for Production
- Activity 3: Understanding Jenkins Production Pipeline Tasks
- Activity 4: Observing Jenkins Production Deployment
- What You’ve Learned
- Activity 5: Understanding the Complete Jenkins Workflow
- What’s Next
Learning Objectives
By the end of this section, you will:
-
Understand how Jenkins production deployments transform from weeks to minutes while maintaining enterprise security
-
Experience GitLab Release workflows that trigger production Jenkins pipelines automatically
-
Learn about enterprise-grade security validation integrated into Jenkins production workflows
-
See how GitOps ensures safe production deployments through Jenkins automation
-
Understand how Jenkins expertise becomes more valuable with enhanced production capabilities
Understanding Jenkins Production Transformation
Enterprise development teams often face substantial challenges with production deployments using traditional Jenkins processes:
Traditional Jenkins Production Challenges
-
2-3 weeks required for manual Jenkins production deployment coordination
-
Multiple approval workflows that create bottlenecks in Jenkins-based delivery
-
Manual security reviews that delay Jenkins production releases
-
Risk of human error during manual Jenkins production deployment processes
-
Inconsistent deployment procedures across different Jenkins production environments
Red Hat Advanced Developer Suite Solution for Jenkins
Red Hat Advanced Developer Suite (RHADS) transforms your Jenkins production experience with:
-
Production deployment time: 2-3 weeks → 30 minutes with automated Jenkins pipelines
-
Preserves millions in Jenkins infrastructure investment while adding modern capabilities
-
Zero manual security reviews through automated policy enforcement in Jenkins workflows
-
Complete SOC 2 and PCI audit trails automatically generated through Jenkins processes
Key Business Benefits for Jenkins Production:
-
Jenkins production deployment time from weeks to minutes
-
Enhanced security validation integrated into familiar Jenkins production workflows
-
Jenkins expertise becomes more valuable with modern production capabilities
-
Complete audit trails for enterprise compliance through Jenkins automation
Activity 1: Understanding Jenkins Production Triggers
RHADS provides flexible production deployment options that work with your existing Jenkins expertise:
Understanding Git Tag vs GitLab Release
Your Jenkins pipeline reacts differently based on the trigger type, providing appropriate control for different environments:
-
Git tag push promotes the image to staging using familiar Jenkins workflows
-
GitLab Release creation triggers production promotion with additional safeguards
This separation allows teams to enforce distinct policies and approval flows for different environments while using the same enhanced Jenkins pipeline infrastructure.
Business Value:
-
Staging Speed: Git tag push enables rapid staging validation through Jenkins
-
Production Control: GitLab Release provides intentional production gate with audit trail
-
Risk Management: Different triggers allow appropriate validation rigor per environment
-
Jenkins Consistency: Same familiar Jenkins pipeline handles both environments
Activity 2: Creating a GitLab Release for Production
Let’s trigger your Jenkins production pipeline using GitLab Release functionality that integrates with your enhanced Jenkins workflows.
Step 1: Access Your GitLab Repository
-
Open your GitLab repository at qrks-jnk-{user}
-
Sign in using:
Username: {gitlab_user} Password: {gitlab_user_password}
Step 2: Create a GitLab Release
Creating a GitLab release triggers your Jenkins production pipeline with enhanced security validation.
-
In the left navigation menu, go to Deploy > Releases
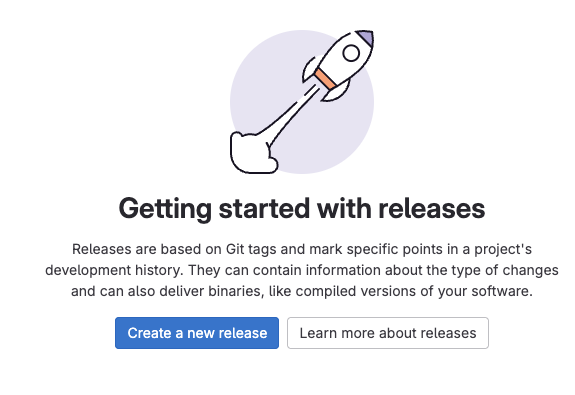
-
Click Create a new release
-
Select the existing tag, such as
v1.0 -
Optionally add release notes
-
Click Create release
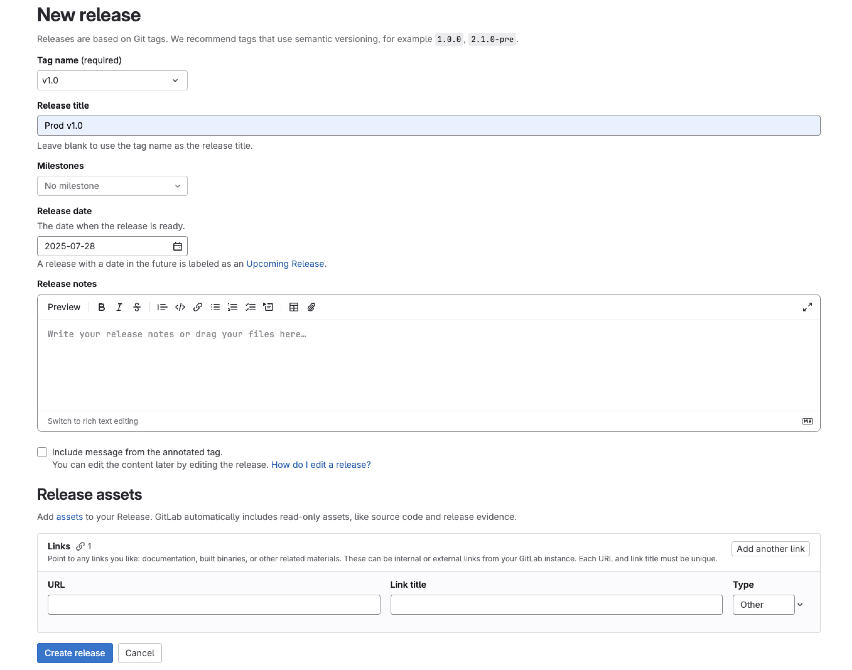
|
This GitLab release creation triggers a webhook that starts your Jenkins production pipeline* The pipeline automatically detects this is a release event and switches into production promotion mode, ensuring the same validated image is promoted to the production environment through Jenkins automation. |
Step 3: Monitor Jenkins Production Pipeline
-
Navigate to Red Hat Developer Hub
-
Go to your
qrks-jnk-{user}component under Catalog > Component
-
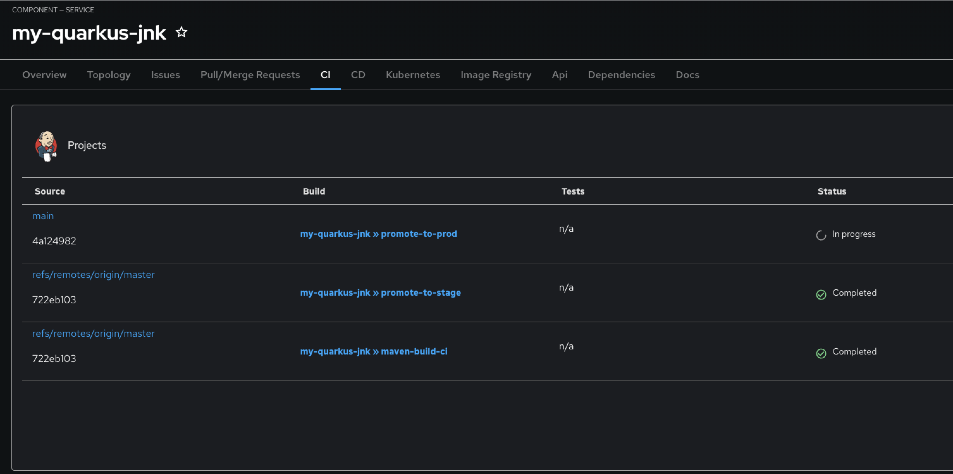
Click the CI tab to see your Jenkins pipeline runs
-
Locate the build labeled promote-to-prod
-
Click on the View build icon to follow progress in Jenkins
-
Click Open Blue Ocean to view the Jenkins production pipeline stages
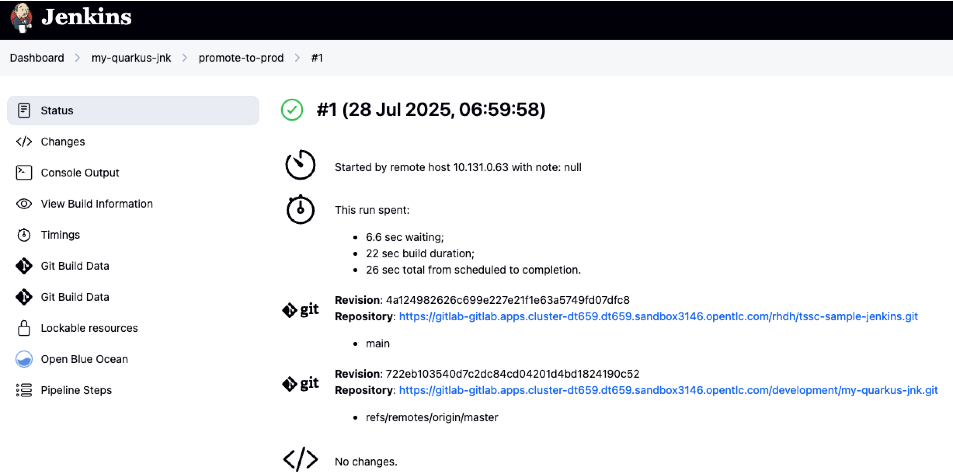
|
The same Jenkins pipeline is reused for both staging and production, but its behavior changes based on the trigger type — demonstrating how enhanced Jenkins workflows provide appropriate safeguards for each environment. |
Activity 3: Understanding Jenkins Production Pipeline Tasks
Your Jenkins production pipeline ensures enterprise-grade security while maintaining familiar workflows* Let’s examine each critical task:
Task 1: gather-images
Purpose: Perfect production traceability through Jenkins workflows
This Jenkins task ensures complete accountability for production deployments:
-
Production Audit Confidence: Regulators can trace every production change to its source through Jenkins
-
Compliance Automation: SOC 2 and PCI requirements satisfied automatically via Jenkins workflows
-
Risk Management: Perfect tracking of what was deployed when production issues arise
-
Investment Leverage: Enhanced traceability through existing Jenkins infrastructure
Technical Implementation:
In the gather-images stage, Jenkins calls the GitLab API to fetch the release tag (e.g* v1.0)* Based on this tag, it constructs the container image URL that was built and signed in the staging phase through Jenkins automation.
Jenkins creates an images.json file to describe the image metadata and where it came from, becoming the source of truth for the production validation step.
Sample images.json for production:
{
"components": [
{
"containerImage": "quay.tssc-quay/tssc/qrks-jnk-{user}:v1.0",
"source": {
"git": {
"url": "https://gitlab-gitlab.apps.cluster-pc8p5.pc8p5.sandbox275.opentlc.com/development/qrks-jnk-{user}",
"revision": "v1.0"
}
}
}
]
}Task 2: verify-ec
Purpose: Critical business protection through automated Jenkins security validation
This Jenkins stage provides the most critical business protection by validating that images are enterprise-ready before production deployment:
Business Value for Jenkins Production:
-
Zero Security Incidents: Automated validation catches issues before customers are affected
-
Compliance Automation: SOC 2, PCI requirements enforced automatically through Jenkins
-
Speed Enhancement: Security validation in minutes vs* weeks using Jenkins workflows
-
Risk Elimination: 100% consistent security enforcement across all Jenkins production deployments
Enterprise Production Security Validations in Jenkins:
-
Verifies signatures (Cosign) integrated with Jenkins security processes
-
Checks for Software Bill of Materials (SBOM) for production supply chain security
-
Confirms supply chain integrity (SLSA provenance) through Jenkins audit trails
-
Runs CVE checks to prevent production vulnerabilities
-
Enforces custom organizational rules through Jenkins policy integration
Technical Implementation in Jenkins:
Jenkins runs the verify-ec stage using the Red Hat Trusted Application Pipeline shared library:
Cosign trust initialization in Jenkins:
cosign initialize \
--mirror https://tuf.tssc-tas.dev \
--root https://tuf.tssc-tas.dev/root.jsonEnterprise Contract validation through Jenkins:
ec validate image \
--policy default \
--public-key k8s://openshift/trusted-keys \
--output json \
--image quay.tssc-quay/tssc/qrks-jnk-{user}:v1.0Sample Jenkins production validation output:
{
"successes": [
"Image is signed and verified with cosign",
"SBOM (CycloneDX) is present",
"Provenance matches repository",
"No critical vulnerabilities found"
],
"failures": []
}|
If any of these production checks fail through Jenkins, the pipeline stops immediately — ensuring no risky code reaches your customers* This automated production security gate protects your business reputation and customer trust. |
Task 3: update-image-tag-for-prod
Purpose: Production quality gateway through Jenkins validation
This Jenkins task ensures only enterprise-validated images receive production designation:
-
Clear Production Intent:
prod-v1.0tag signals security validation complete through Jenkins -
Audit Trail: Complete traceability from source code to production via Jenkins workflows
-
Risk Mitigation: Only validated, compliant images reach customers through Jenkins processes
-
Operational Clarity: Teams know instantly which images are production-approved via Jenkins
Technical Implementation in Jenkins:
Jenkins uses skopeo to copy the image and apply a production tag with the prod- prefix:
skopeo copy \
docker://quay.tssc-quay/tssc/qrks-jnk-{user}:v1.0 \
docker://quay.tssc-quay/tssc/qrks-jnk-{user}:prod-v1.0This Jenkins step doesn’t rebuild the image* It simply re-tags a verified, immutable image — ensuring complete traceability and production readiness confidence.
By tagging it prod-v1.0 through Jenkins automation, we make it clear to downstream systems, release teams, and auditors that:
- The image has passed all enterprise validations through Jenkins
- It’s safe and approved for production deployment
- Its origin and promotion path are completely transparent via Jenkins audit trails
Task 4: deploy-to-prod
Purpose: Automated production bridge through Jenkins and GitOps integration
This Jenkins task ensures validated changes reach production automatically without manual intervention:
-
Zero Manual Errors: GitOps automation eliminates deployment mistakes in Jenkins production workflows
-
100% Audit Trail: Every production change tracked and traceable through Jenkins processes
-
Consistent Process: Same Jenkins deployment method for routine and emergency production changes
-
Risk Elimination: No manual steps that could introduce errors during critical production releases
Technical Implementation through Jenkins:
In the deploy-to-prod stage, Jenkins uses rhtap.update_deployment() to patch the kustomization.yaml overlay for production* This updates the image tag in the deployment-patch.yaml to reference the new production-approved image.
Jenkins commits and pushes this change to the GitOps repository under the overlays/prod/ directory.
deployment-patch.yaml updated by Jenkins:
apiVersion: apps/v1
kind: Deployment
metadata:
name: qrks-jnk-{user}
spec:
template:
spec:
containers:
- name: qrks-jnk-{user}
image: quay.tssc-quay/tssc/qrks-jnk-{user}:prod-v1.0Argo CD continuously watches this GitOps repository* Once it detects Jenkins updates: - It syncs the production manifests - Deploys the new image to the production cluster - No manual approval or CLI interaction is needed
This final Jenkins step completes the production promotion workflow — fully automated, fully auditable, and GitOps-native while preserving Jenkins expertise.
Activity 4: Observing Jenkins Production Deployment
Watch how your Jenkins pipeline safely deploys to production using enterprise-grade validation and GitOps automation.
Step 1: Monitor Jenkins Pipeline Execution
-
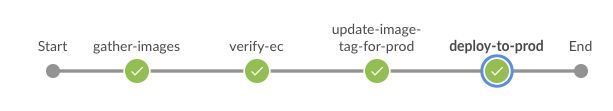
In Jenkins Blue Ocean, observe each production stage completing:
-
gather-images: Jenkins identifies the exact production image to deploy
-
verify-ec: Jenkins validates enterprise security policies for production
-
update-image-tag-for-prod: Jenkins tags the image as production-ready
-
deploy-to-prod: Jenkins updates production GitOps manifests automatically
-
-
Notice how Jenkins provides familiar monitoring interfaces while handling enterprise production workflows
Step 2: Verify Production GitOps Integration
-
Access your GitOps repository at qrks-jnk-{user}-gitops
-
Check the updated deployment manifests in the
overlays/proddirectory -
Notice how Jenkins automatically updated the image tag with the
prod-prefix -
Observe the Git diff showing the automated production update through Jenkins
Example Git diff generated by Jenkins:
- image: quay.io/redhat-appstudio/rhtap-task-runner:latest
+ image: quay.tssc-quay/tssc/qrks-jnk-{user}:prod-v1.0Step 3: Monitor Production Deployment Success
-
ArgoCD automatically detects the production changes made by your Jenkins pipeline
-
ArgoCD syncs these validated changes to the production environment
-
The production deployment completes successfully without manual intervention
Step 4: Validate Production Application
-
Access your production application through its route
-
Verify that your changes are live and functioning correctly in production
-
Confirm that the production environment reflects exactly what Jenkins validated
-
Test production functionality to ensure successful enterprise deployment
What You’ve Learned
You’ve experienced how Red Hat Advanced Developer Suite transforms enterprise Jenkins production deployments while preserving valuable investment and expertise:
Jenkins Production Pipeline Summary
| Jenkins Task | Purpose |
|---|---|
gather-images |
Jenkins pulls production image from staging using Git tag and builds production |
verify-ec |
Jenkins validates image using EC policies — checking signatures, SBOM, provenance, and CVEs for production |
update-image-tag-for-prod |
Jenkins re-tags validated image with |
deploy-to-prod |
Jenkins updates |
Key Business Transformation for Jenkins Production
Enhanced Jenkins Production Benefits:
-
Deployment Speed: Jenkins production releases from 2-3 weeks → 30 minutes
-
Investment Protection: Jenkins infrastructure and expertise enhanced rather than replaced
-
Security Automation: 100% automated policy enforcement through enhanced Jenkins workflows
-
Risk Elimination: Enterprise-grade security without disrupting proven Jenkins production processes
Enterprise Production Security through Jenkins:
-
Automated security validation integrated into familiar Jenkins production workflows
-
Complete audit trails for compliance requirements through Jenkins processes
-
Cryptographic proof of production image integrity and source via Jenkins pipelines
-
Consistent security enforcement across all Jenkins production deployments
Jenkins Investment Enhancement for Production:
-
Existing Jenkins production infrastructure becomes more powerful and valuable
-
Jenkins production expertise enhanced with modern security and GitOps capabilities
-
Teams continue using familiar Jenkins tools for production with enhanced automation
-
Platform efficiency improves while preserving critical Jenkins production knowledge
Activity 5: Understanding the Complete Jenkins Workflow
Now that you’ve seen the complete development to production flow, let’s review the integrated Jenkins experience:
Development to Production Jenkins Flow
| Environment | Jenkins Trigger | Pipeline | Validation Level |
|---|---|---|---|
Development |
|
|
Code quality, unit tests, basic security scan |
Staging |
|
|
Enterprise Contract validation, comprehensive security |
Production |
GitLab Release |
|
Final validation, production-ready verification |
Jenkins Enhancement Value Proposition
For Jenkins Teams:
-
Familiar Tools: Continue using Jenkins Blue Ocean, pipeline syntax, and troubleshooting approaches you know
-
Enhanced Capabilities: Gain enterprise security, GitOps, and compliance automation within Jenkins
-
Preserved Investment: Leverage existing Jenkins infrastructure, expertise, and operational knowledge
-
Modern Integration: Bridge Jenkins CI with modern GitOps CD patterns seamlessly
For Enterprise Leadership:
-
ROI Protection: Jenkins investments enhanced rather than replaced
-
Risk Reduction: Enterprise security automatically enforced in all Jenkins workflows
-
Compliance Automation: SOC 2, PCI, and audit requirements met through Jenkins processes
-
Competitive Advantage: Deploy faster with higher confidence using enhanced Jenkins capabilities
What’s Next
Congratulations! You’ve successfully experienced the complete Jenkins enhancement journey with Red Hat Advanced Developer Suite:
What You Accomplished
-
Self-Service Application Creation: Generated complete Jenkins applications in minutes instead of weeks
-
Enhanced Security Integration: Experienced enterprise security seamlessly integrated into Jenkins workflows
-
Automated Staging Validation: Triggered sophisticated validation through simple Git tags in Jenkins
-
Safe Production Deployment: Deployed to production with enterprise confidence through enhanced Jenkins
-
Preserved Jenkins Expertise: Used familiar Jenkins tools enhanced with modern capabilities
Business Impact Realized
-
Jenkins Pipeline Setup: 1-2 weeks → 5 minutes with self-service templates
-
Security Integration: Manual coordination → Automatic enforcement in Jenkins workflows
-
Staging Validation: 3-5 days → 30 minutes through enhanced Jenkins automation
-
Production Deployment: 2-3 weeks → 30 minutes with Jenkins-driven GitOps
Enterprise Benefits Delivered
-
Investment Protection: Enhanced Jenkins capabilities preserve infrastructure and team expertise
-
Security Excellence: Enterprise-grade security integrated into familiar Jenkins workflows
-
Operational Efficiency: Platform teams focus on innovation rather than Jenkins maintenance
-
Competitive Advantage: Faster, safer delivery through enhanced Jenkins automation
The transformation demonstrates how Red Hat Advanced Developer Suite enhances rather than replaces your valuable Jenkins investment, making your Jenkins expertise more valuable while delivering enterprise security and modern development capabilities.