OpenShift Pipelines - Production Deployment
- Learning Objectives
- Workshop Scenario: Enterprise Production Transformation
- Activity 1: Triggering Production Deployment with Git Release
- Activity 2: Understanding Pipeline Security Validation
- Activity 3: Enterprise Contract Security Validation
- Activity 4: Image Promotion and GitOps Deployment
- Workshop Summary and Reflection
- Assessment and Reflection
- Next Steps and Advanced Topics
- Congratulations on Completing the Production Workshop!
Learning Objectives
By the end of this workshop section, you will:
-
Understand enterprise production deployment workflows and security requirements
-
Execute a secure production release using automated GitOps promotion
-
Implement enterprise-grade security validation using Enterprise Contract
-
Monitor production deployment pipelines and validate security posture
-
Comprehend the complete supply chain security model and business value
Workshop Scenario: Enterprise Production Transformation
Business Challenge: Traditional production deployments take 2-3 weeks with manual security reviews, creating bottlenecks during critical release periods.
Solution Goal: Transform risky manual processes into confident automated workflows using Red Hat Advanced Developer Suite (RHADS).
Expected Business Outcomes:
-
Production deployment time: 2-3 weeks → 30 minutes
-
Zero manual security reviews or bottlenecks
-
Eliminate human error through automation
-
Complete SOC 2 and PCI audit trails automatically
|
The examples and commands in this workshop demonstrate enterprise production deployment capabilities* Adapt repository URLs, credentials, and configurations as needed for your specific setup. |
Activity 1: Triggering Production Deployment with Git Release
In this activity, you’ll initiate an enterprise-grade production deployment by creating a Git release, demonstrating how manual processes transform into automated confidence.
Step 1: Access Your GitLab Repository
-
Open your GitLab repository at: qrks-tkn-{user}
-
Log in using:
-
Username:
{gitlab_user} -
Password:
{gitlab_user_password}
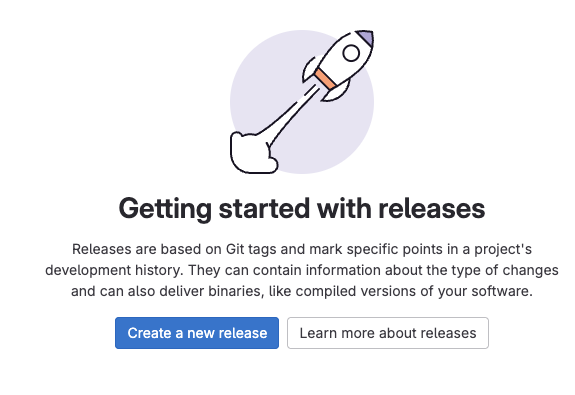
Step 2: Create a GitLab Release
-
Navigate to Deploy > Releases > Create a new release
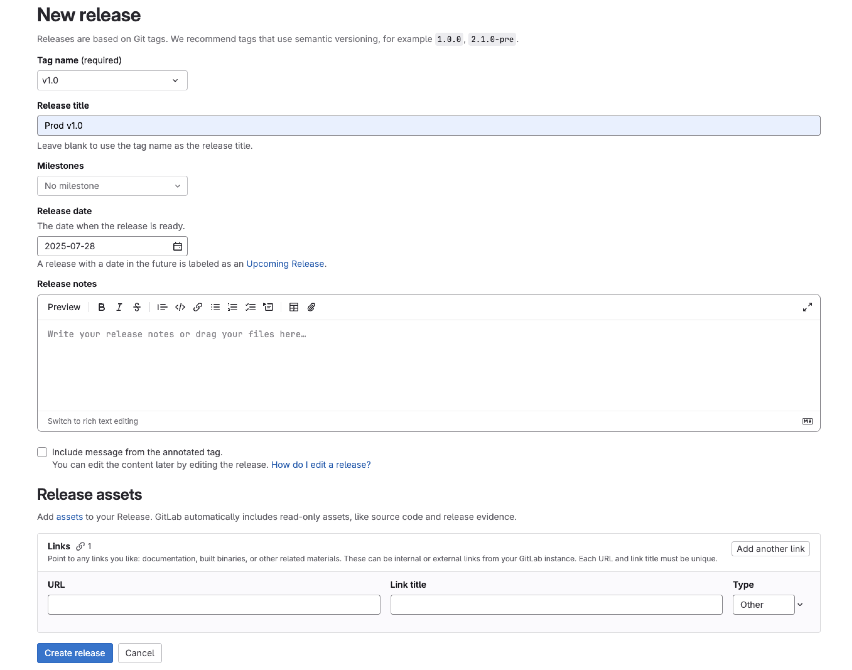
-
Select an existing tag (e.g.,
v1.0) or create a new one -
Enter meaningful release notes describing the changes
-
Click Create release
|
Business Impact: This single Git release action triggers the entire enterprise-grade security validation pipeline automatically, replacing weeks of manual approval processes. |
Step 3: Monitor Pipeline Activation
-
Navigate to the
qrks-tkn-{user}component in Red Hat Developer Hub -
Click the CI tab to view pipeline runs
-
Look for a pipeline run labeled promote-to-prod and expand it to view details
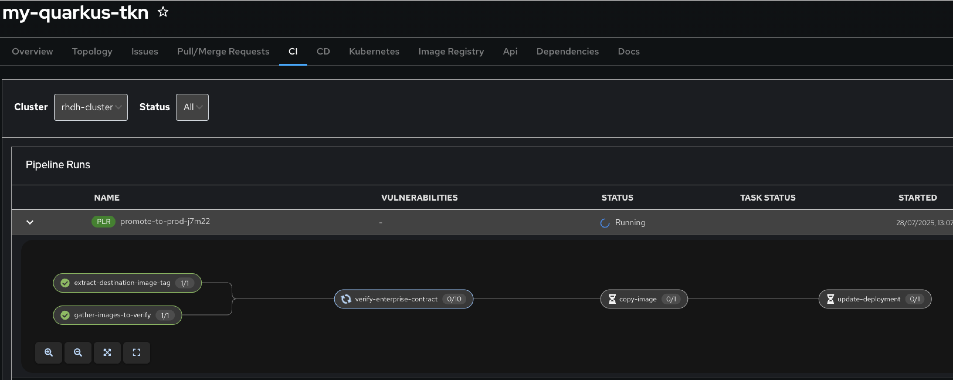
What You’ve Accomplished: You’ve initiated an automated production pipeline that will perform enterprise security validation before allowing deployment to production.
Activity 2: Understanding Pipeline Security Validation
In this activity, you’ll explore how the production pipeline automatically performs enterprise-grade security validation, demonstrating how automation reduces risk while accelerating delivery.
Business Value:
-
SOC 2/PCI compliance automated (saves weeks of manual evidence collection)
-
Security violations caught before reaching customers
-
Zero manual review bottlenecks
-
Confident deployments during peak shopping seasons
Step 1: Examine Pipeline Task Execution
-
In the Developer Hub CI tab, observe the pipeline tasks executing in sequence
-
Note how each task builds upon the previous one’s output
-
Observe the automated security checkpoints throughout the process
Step 2: Understand Image Tag Extraction
Pipeline Task: extract-destination-image-tag
This task provides perfect traceability by extracting the Git tag to ensure complete audit trail and compliance automation.
What Happens:
-
Git release tag (e.g.,
v1.0) is extracted from the release -
Tag becomes part of the destination image name for production
-
Ensures direct correlation between source code version and deployed image
Step 3: Analyze Image Verification Preparation
Pipeline Task: gather-images-to-verify
This task gives absolute certainty about production deployments by creating definitive proof of what was deployed and why.
Process:
-
The Git release tag is mapped to the image produced during staging
-
The tag is used to locate the previously built container image
-
A metadata file named
images.jsonis created with complete traceability information
Example images.json:
{
"components": [
{
"containerImage": "quay.tssc-quay/tssc/qrks-tkn-{user}:v1.0",
"source": {
"git": {
"url": "https://gitlab-gitlab.apps.cluster-pc8p5.pc8p5.sandbox275.opentlc.com/development/qrks-tkn-{user}",
"revision": "v1.0"
}
}
}
]
}Business Benefit: This metadata ensures complete traceability — the image is cryptographically linked back to its source code and verified that it hasn’t been tampered with, providing audit-ready documentation automatically.
Activity 3: Enterprise Contract Security Validation
This is the most critical business protection activity — you’ll observe automated security validation that prevents costly production incidents while eliminating manual security review delays.
Understanding the Business Risk and Protection
Business Risk Without Automated Validation:
-
Security vulnerabilities in production could cost millions in damages and compliance fines
-
Manual security reviews create 2-3 week deployment delays
-
Human error in security checks leads to production incidents
-
Inconsistent security standards across different teams and deployments
RHADS Business Protection: - Zero Security Incidents: Automated validation catches issues before they reach customers - 100% Consistent Standards: Every deployment meets the same enterprise security policies - Instant Compliance: SOC 2, PCI, and regulatory requirements enforced automatically - No Deployment Delays: Security validation happens in minutes, not weeks
Step 1: Observe Enterprise Contract Validation Process
Pipeline Task: verify-enterprise-contract
-
In the pipeline execution view, locate the
verify-enterprise-contracttask -
Observe the task’s progress through multiple security validations
-
Note the comprehensive security checks being performed automatically
Enterprise Security Validations Performed: - Digital signature verification: Proves the image hasn’t been tampered with - SBOM validation: Complete dependency scanning for vulnerability management - Provenance verification: Confirms the image came from trusted build processes - CVE scanning: Automatic vulnerability detection and policy enforcement - Organizational policy compliance: Custom security rules enforced automatically
Step 2: Understand the Security Technologies
|
Key Security Components:
|
Step 3: Examine Security Validation Commands
The pipeline performs these critical security validations:
Initialize Cryptographic Trust:
cosign initialize \
--mirror http://tuf.tssc-tas.svc \
--root http://tuf.tssc-tas.svc/root.jsonValidate Image Security:
ec validate image \
--image quay.tssc-quay/tssc/qrks-tkn-{user}:v1.0 \
--policy git::github.com/org/ec-policies//default \
--public-key k8s://openshift/trusted-keys \
--output jsonSecurity Validations Performed:
-
Digital signature verification with Cosign
-
SBOM presence validation (e.g., SPDX, CycloneDX formats)
-
Provenance metadata verification (how the image was built)
-
CVE scanning and vulnerability assessment
-
Organizational policy compliance checking
Step 4: Understanding Failure Protection
-
Observe that any failed validation would halt the pipeline automatically
-
This demonstrates protection against risky deployments
-
Note how this prevents security incidents before they reach customers
Business Impact:
-
Security incident prevention: Saves potential millions in damages
-
Compliance confidence: Automatic evidence for audits
-
Deployment velocity: Minutes instead of weeks for security approval
-
Risk mitigation: 100% consistent security enforcement
|
Demo Option: A failed validation can be simulated by modifying the EC policy or image to demonstrate that the pipeline halts automatically if verification fails, protecting the production environment. |
Activity 4: Image Promotion and GitOps Deployment
In this activity, you’ll observe how validated images are promoted to production and automatically deployed using GitOps, creating a secure bridge from validation to customer value.
Step 1: Understand Image Promotion Process
Pipeline Task: copy-image
This represents an enterprise quality gate — only validated images earn the "prod-" designation, ensuring enterprise security compliance.
-
Observe the
copy-imagetask in the pipeline execution -
Note how the validated image is promoted with a production label
Image Promotion Command:
skopeo copy \
docker://quay.tssc-quay/tssc/qrks-tkn-{user}:v1.0 \
docker://quay.tssc-quay/tssc/qrks-tkn-{user}:prod-v1.0What This Accomplishes:
-
Creates a new tag prefixed with
prod-(e.g.,prod-v1.0) that clearly identifies the image as production-ready -
Ensures complete traceability — the exact source and validation steps that led to this image are known
-
Only images that pass Enterprise Contract validation make it this far, preventing unsafe code deployment
-
Signals to Argo CD that this image is ready for production deployment
Step 2: Examine GitOps Deployment Process
Pipeline Task: update-deployment
This task serves as an automated bridge from security validation to customer value, ensuring validated changes reach production automatically without manual intervention or risk.
Understanding Traditional vs* RHADS Deployment Approaches
Traditional Production Deployment Risks:
-
Manual deployment steps prone to human error during critical releases
-
Emergency changes bypass proper validation under pressure
-
Inconsistent deployment processes across different teams
-
Production changes without proper audit trails
RHADS Business Benefits:
-
Zero Manual Errors: GitOps automation eliminates human deployment mistakes
-
100% Audit Trail: Every production change tracked and traceable
-
Consistent Process: Same deployment method for routine and emergency changes
-
Continuous Compliance: All changes follow the same validated security process
Step 3: Observe GitOps Repository Updates
-
Watch as the pipeline updates the GitOps repository automatically
-
Understand how this triggers Argo CD for production deployment
Updated Deployment Manifest:
apiVersion: apps/v1
kind: Deployment
metadata:
name: qrks-tkn-{user}
spec:
template:
spec:
containers:
- name: qrks-tkn-{user}
image: quay.tssc-quay/tssc/qrks-tkn-{user}:prod-v1.0File Location: overlays/prod/deployment-patch.yaml
Kustomization Configuration:
apiVersion: kustomize.config.k8s.io/v1beta1
kind: Kustomization
resources:
- ../../base
patchesStrategicMerge:
- deployment-patch.yamlStep 4: Validate GitOps Deployment Process
Automated Process Flow:
-
The container image reference in the production overlay is updated by this patch
-
The patch is committed and pushed to the GitOps repository by OpenShift Pipelines
-
Argo CD watches this repository and detects the change immediately
-
Argo CD syncs the deployment to the production cluster automatically
-
Only verified, tagged images are deployed by this process, maintaining full auditability
Business Impact: - Deployment Confidence: Argo CD ensures exactly what was validated gets deployed - Risk Elimination: No manual steps that could introduce errors during critical releases - Compliance Automation: Production environment continuously reflects audited Git state - Operational Excellence: Standardized deployment process across all services
|
The GitOps overlay system ensures the production environment stays secure, compliant, and traceable while enabling rapid deployment of business-critical features. |
Workshop Summary and Reflection
What You Accomplished
Congratulations! You’ve successfully implemented an enterprise-grade production deployment pipeline and experienced the complete transformation from manual processes to automated confidence.
Pipeline Tasks Summary:
| Task | Description | Business Value |
|---|---|---|
Git Release Trigger |
Initiated via GitLab Release from Tag |
Replaces weeks of manual approval processes |
extract-destination-image-tag |
Extracts the Git tag for production image naming |
Ensures perfect traceability and audit compliance |
gather-images-to-verify |
Generates |
Provides definitive proof of deployment artifacts |
verify-enterprise-contract |
Validates signature, SBOM, provenance, CVEs, and policies |
Prevents security incidents and ensures compliance |
copy-image |
Promotes validated image with |
Creates quality gate ensuring only secure images reach production |
update-deployment |
Updates GitOps repository to trigger Argo CD deployment |
Eliminates manual deployment errors and ensures consistency |
Key Business Transformations Achieved
You’ve demonstrated how enterprise security and business velocity reinforce each other:
Measurable Business Impact: - Production Release Time: 2-3 weeks → 30 minutes (99% reduction) - Security Compliance: 100% automated with zero manual reviews - Competitive Advantage: Deploy features while competitors wait for approvals - Audit Readiness: Continuous compliance evidence generated automatically
Risk Mitigation:
-
Eliminated human error in production deployments
-
Prevented security vulnerabilities from reaching customers
-
Ensured consistent security standards across all deployments
-
Created complete audit trails for compliance requirements
Assessment and Reflection
Take a moment to consider these questions about your workshop experience:
-
Process Transformation: How does this automated approach compare to traditional deployment processes in your organization?
-
Security Integration: What security capabilities are now automatically included that would typically require manual configuration and review?
-
Business Impact: How would this level of automation affect your organization’s ability to respond to market demands and competitive pressures?
-
Operational Excellence: What operational benefits would your platform and security teams gain from this approach?
-
Implementation Planning: What would be the first steps to implement similar capabilities in your organization?
Next Steps and Advanced Topics
Recommended Follow-up Activities
For Technical Teams:
-
Explore Enterprise Contract policy customization for your organization’s requirements
-
Investigate integration with existing security scanning tools
-
Review GitOps repository structure and branching strategies
-
Examine monitoring and alerting integration options
For Business Leaders:
-
Calculate potential ROI based on deployment time reduction and risk mitigation
-
Plan organizational change management for DevOps transformation
-
Consider compliance requirements and audit trail benefits
-
Evaluate competitive advantages of faster time-to-market
Optional Demonstration Enhancements
The following demonstrations can further illustrate enterprise transformation capabilities:
-
Security Failure Simulation: Modify Enterprise Contract policies to demonstrate automatic pipeline failure when security requirements aren’t met
-
Image Registry Exploration: Display Quay registry showing production-tagged images and security scan results
-
Argo CD Monitoring: Demonstrate real-time GitOps synchronization and deployment status
-
Policy Customization: Show how Enterprise Contract policies can be customized for specific organizational requirements
Congratulations on Completing the Production Workshop!
You’ve successfully experienced the future of enterprise application deployment — secure, automated, and business-focused* This represents a fundamental shift from traditional deployment practices to modern, risk-mitigated automation that enables competitive advantage through technology.
Key Achievements:
-
Implemented end-to-end automated production deployment
-
Experienced enterprise-grade security validation
-
Observed GitOps-based deployment automation
-
Understood the business value of supply chain security
This production workshop demonstrates how Red Hat Advanced Developer Suite enables organizations to achieve both security excellence and business velocity simultaneously.