Jenkins Pipelines - Staging
Learning Objectives
By the end of this section, you will:
-
Understand how Jenkins staging validation transforms development cycles from days to minutes
-
Experience enterprise-grade security validation with Enterprise Contract integrated into Jenkins workflows
-
Trigger Jenkins staging pipelines using Git tags and observe automated promotion workflows
-
Learn how GitOps ensures validated changes reach staging environments through Jenkins automation
-
See how Jenkins expertise becomes more valuable with enhanced staging capabilities
Understanding Jenkins Staging Transformation
Enterprise development teams with significant Jenkins investments often face substantial challenges with staging validation processes:
Traditional Jenkins Staging Challenges
-
3-5 days required for manual Jenkins staging coordination and deployment
-
1-2 weeks for manual security reviews and compliance checks in Jenkins workflows
-
Multiple coordination meetings between development, platform, and security teams for Jenkins staging
-
Manual Jenkins staging processes that are error-prone and time-consuming
-
Inconsistent Jenkins configurations across different staging environments
Red Hat Advanced Developer Suite Solution for Jenkins
Red Hat Advanced Developer Suite (RHADS) transforms your Jenkins staging experience with:
-
Staging time: 3-5 days → 30 minutes with automated Jenkins validation pipelines
-
Security validation: 1-2 weeks → minutes with integrated Enterprise Contract in Jenkins workflows
-
Zero manual coordination overhead while preserving Jenkins expertise
-
Production-ready confidence with every Jenkins staging deployment
-
Enhanced Jenkins capabilities that make your existing skills more valuable
Key Business Benefits for Jenkins Teams:
-
Jenkins staging deployment time from days to minutes
-
Enhanced security validation integrated into familiar Jenkins workflows
-
Jenkins expertise becomes more valuable with modern capabilities
-
Platform teams focus on innovation instead of manual Jenkins coordination
Activity 1: Triggering the Jenkins Staging Pipeline
Let’s create a Git tag to trigger your automated Jenkins staging pipeline and observe how enterprise validation works within familiar Jenkins workflows.
Step 1: Access Your GitLab Repository
-
Open your GitLab repository at qrks-jnk-{user}
-
Sign in using:
Username: {gitlab_user} Password: {gitlab_user_password}
Step 2: Create a Git Tag for Jenkins Staging
Creating a Git tag triggers your Jenkins staging pipeline, demonstrating how simple actions can activate sophisticated workflows.
-
In the left menu, click on Code > Tags > New Tag
-
Enter a version tag like
v1.0 -
Choose the target branch (typically
main) -
Click Create Tag
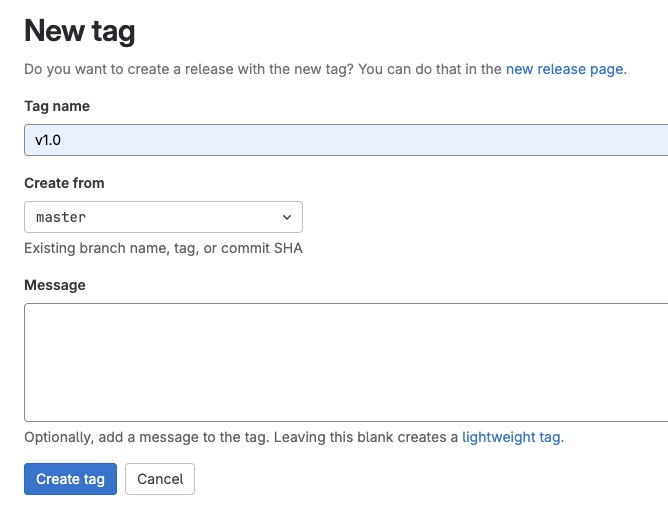
|
This tag creation triggers a GitLab webhook that activates your Jenkins staging pipeline — the one that promotes the image to the staging environment with enterprise security validation. |
Alternative: CLI Approach for Jenkins
If you prefer the command line approach that many Jenkins users are comfortable with:
git tag v1.0
git push --tagsThis CLI method triggers the same Jenkins staging automation while maintaining the familiar developer workflow.
Step 3: Monitor Jenkins Pipeline Execution
-
Navigate to Red Hat Developer Hub
-
Go to your
qrks-jnk-{user}component -
Click the CI tab to see your Jenkins pipeline runs
-
Look for the job labeled promote-to-stage and click View build to follow its progress
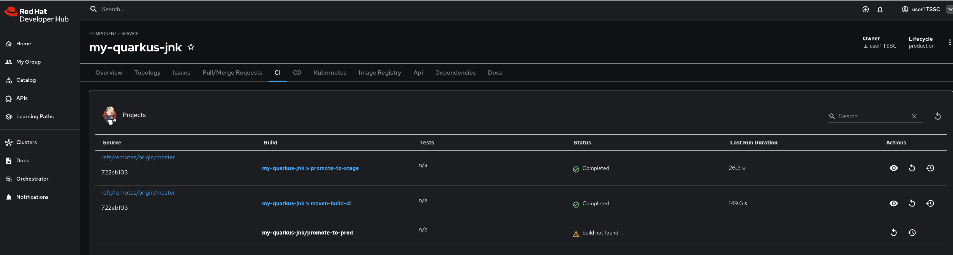
-
Click Open Blue Ocean to view the Jenkins pipeline stages in the familiar interface
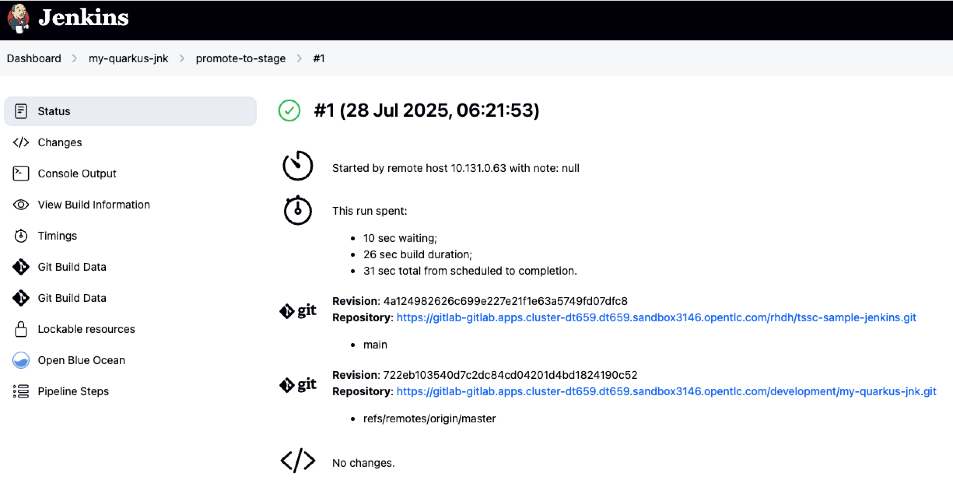
|
Use the Developer Hub view combined with Jenkins Blue Ocean to observe each task as it executes* You’ll see enterprise automation in action using familiar Jenkins tools — no manual approvals, just policy-driven promotion through enhanced Jenkins workflows. |
Activity 2: Understanding Jenkins Pipeline Tasks
Your Jenkins staging pipeline provides production-level confidence while eliminating manual bottlenecks and preserving your Jenkins expertise* Let’s examine each task in detail.
Task 1: gather-images
Purpose: Perfect traceability through Git tags in Jenkins workflows
This Jenkins task identifies exactly what needs to be promoted by:
-
Resolving the Git tag back to its commit ID for precise tracking
-
Matching the commit to the corresponding container image built in development
-
Creating an authoritative
images.jsonfile for the Jenkins validation process
Business Value for Jenkins Teams: - Complete Staging Traceability: Every Jenkins staging deployment links to specific code changes - Quality Assurance: Jenkins staging validates exactly what will reach production - Audit Readiness: Complete Jenkins staging evidence trail for compliance reviews - Development Confidence: Teams know precisely what’s being validated in Jenkins staging
Sample images.json generated by Jenkins:
{
"components": [
{
"containerImage": "quay.tssc-quay/tssc/qrks-jnk-{user}:123456",
"source": {
"git": {
"url": "https://gitlab-gitlab.apps.cluster-pc8p5.pc8p5.sandbox275.opentlc.com/development/qrks-jnk-{user}",
"revision": "123456"
}
}
}
]
}This mapping provides end-to-end traceability through your Jenkins workflow — you know exactly what code went into what image during staging validation.
Task 2: verify-ec
Purpose: Critical business protection through automated security validation in Jenkins
This Jenkins stage enforces multiple critical validations that protect your business and customers while leveraging familiar Jenkins workflows:
Enterprise Security Validations in Jenkins: - Digital signature verification using cryptographic signing integrated with Jenkins - Software Bill of Materials (SBOM) validation for supply chain security - CVE scanning to catch security vulnerabilities before production - Organizational policy compliance ensuring enterprise security standards - Provenance attestation to verify source repository integrity
Business Value for Jenkins Teams: - Zero Jenkins Staging Security Incidents: Automated validation catches issues before production - 100% Consistent Standards: Every Jenkins staging deployment meets enterprise security policies - Instant Staging Validation: Security validation in Jenkins staging happens in minutes, not weeks - Production Confidence: Only security-validated features progress from Jenkins staging
Technical Implementation in Jenkins:
Jenkins runs the verify-ec stage using the Red Hat Trusted Application Pipeline shared library:
First, Jenkins initializes Cosign trust using a TUF server:
cosign initialize \
--mirror https://tuf.tssc-tas.dev \
--root https://tuf.tssc-tas.dev/root.jsonThen Jenkins validates the image using Enterprise Contract:
ec validate image \
--policy git::github.com/org/ec-policies//default \
--public-key k8s://openshift/trusted-keys \
--output json \
--image quay.tssc-quay/tssc/qrks-jnk-{user}:123456Sample Jenkins validation output:
{
"successes": [
"Image is signed and verified with cosign",
"SBOM (CycloneDX) is present",
"Provenance matches repository",
"No critical vulnerabilities found"
],
"failures": []
}|
If any security check fails, your Jenkins pipeline stops immediately — ensuring no risky code progresses to the next stage* This automated security gate in Jenkins protects your business without manual intervention. |
Task 3: update-image-tag-for-stage
Purpose: Quality gateway ensuring only validated images reach staging through Jenkins
This Jenkins task promotes the validated image with a human-readable tag (e.g., v1.0), ensuring:
-
Clear Staging Intent: Release version tag signals this image passed all enterprise security checks in Jenkins staging
-
Feature Validation: Complete traceability from source code to staging deployment through Jenkins
-
Quality Assurance: Only validated, compliant features tested in staging through Jenkins workflows
-
Production Preview: Staging becomes accurate production preview using Jenkins-validated images
Technical Implementation in Jenkins:
Jenkins uses skopeo to copy the image and apply the new tag:
skopeo copy \
docker://quay.tssc-quay/tssc/qrks-jnk-{user}:123456 \
docker://quay.tssc-quay/tssc/qrks-jnk-{user}:v1.0|
This Jenkins process guarantees that only validated artifacts are promoted — no unauthorized image changes slip through to staging. |
Task 4: deploy-to-stage
Purpose: Automated GitOps bridge for immediate feature validation through Jenkins
This Jenkins task ensures validated changes reach staging automatically through GitOps integration:
-
Zero Manual Errors: GitOps automation eliminates human staging deployment mistakes in Jenkins workflows
-
100% Staging Audit Trail: Every staging change tracked and traceable through Jenkins
-
Consistent Process: Same Jenkins staging deployment method for routine and emergency features
-
Continuous Validation: All staging changes follow the same validated Jenkins security process
GitOps Implementation through Jenkins:
Jenkins updates the staging deployment configuration automatically:
The pipeline uses rhtap.update_deployment() to patch the kustomization.yaml overlay for stage:
kustomization.yaml:
apiVersion: kustomize.config.k8s.io/v1beta1
kind: Kustomization
resources:
- ../../base
patchesStrategicMerge:
- deployment-patch.yamldeployment-patch.yaml:
apiVersion: apps/v1
kind: Deployment
metadata:
name: qrks-jnk-{user}
spec:
template:
spec:
containers:
- name: qrks-jnk-{user}
image: quay.tssc-quay/tssc/qrks-jnk-{user}:v1.0Jenkins commits and pushes this change to the GitOps repository, and Argo CD detects the update and syncs the deployment to the stage environment automatically.
|
No manual |
Activity 3: Observing Jenkins-Integrated GitOps Deployment
Watch how your Jenkins pipeline integrates with ArgoCD to automatically sync validated changes to the staging environment.
Step 1: Monitor Jenkins Pipeline Progress
-
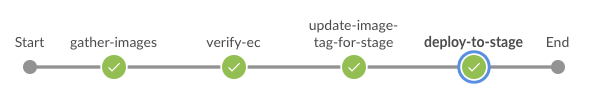
In Jenkins Blue Ocean, observe each stage completing:
-
gather-images: Jenkins identifies the exact image to promote
-
verify-ec: Jenkins validates enterprise security policies
-
update-image-tag-for-stage: Jenkins tags the validated image
-
deploy-to-stage: Jenkins updates GitOps manifests automatically
-
-
Notice how the Jenkins interface provides familiar monitoring while handling modern GitOps workflows
Step 2: Verify GitOps Integration
-
Access your GitOps repository at qrks-jnk-{user}-gitops
-
Check the updated deployment manifests in the
overlays/stagedirectory -
Notice how Jenkins automatically updated the image tag to your release version
-
Observe that this GitOps integration happens seamlessly within Jenkins workflows
What You’ve Learned
You’ve experienced how Red Hat Advanced Developer Suite transforms enterprise Jenkins staging validation while preserving valuable team expertise:
Jenkins Pipeline Task Summary
| Jenkins Task | Purpose |
|---|---|
gather-images |
Jenkins identifies exact image to promote based on Git tag and commit ID |
verify-ec |
Jenkins validates signature, SBOM, provenance, CVEs using Enterprise Contract CLI |
update-image-tag-for-stage |
Jenkins promotes validated image with human-readable tag (e.g., |
deploy-to-stage |
Jenkins updates GitOps repository to trigger Argo CD deployment automatically |
Key Business Transformation for Jenkins Teams
Enhanced Jenkins Staging Benefits:
-
Jenkins staging time: 3-5 days → 30 minutes using familiar tools
-
Production-grade validation catches issues early through Jenkins workflows
-
Zero manual coordination overhead while preserving Jenkins expertise
-
Teams trust Jenkins staging validation represents production reality
Enterprise Security Excellence in Jenkins:
-
Automated security validation integrated into familiar Jenkins workflows
-
Complete audit trails for compliance requirements through Jenkins processes
-
Cryptographic proof of image integrity and source via Jenkins pipelines
-
Consistent security enforcement across all Jenkins deployments
Jenkins Investment Enhancement:
-
Existing Jenkins infrastructure becomes more powerful and valuable
-
Jenkins expertise enhanced with modern security and GitOps capabilities
-
Teams continue using familiar Jenkins tools with enhanced automation
-
Platform efficiency improves while preserving Jenkins knowledge and investment
What’s Next
Your application is now successfully validated and running in staging with enterprise-grade security through enhanced Jenkins workflows!
In the next section, Production - Jenkins Pipeline Deployment, you’ll experience:
-
Production deployment using familiar Jenkins tools with enhanced security
-
Advanced monitoring and observability integrated with Jenkins workflows
-
Complete audit trails that satisfy enterprise compliance requirements through Jenkins
-
Zero-downtime deployment strategies for production environments using Jenkins automation
The transformation from days-long staging cycles to 30-minute automated validation demonstrates how Red Hat Advanced Developer Suite enhances rather than replaces your valuable Jenkins investment and expertise.