Red Hat Lightspeed via the Hybrid Cloud Console - Detect Malware
The Red Hat Lightspeed team also wanted to highlight the Malware detection service available in Red Hat Lightspeed on the Hybrid Cloud Console.
In this module you will evaluate your system for the potential presence of Malware using the Red Hat Lightspeed Malware detection service.
Red Hat has partnered with IBM X-Force Threat Intelligence to access their malware signatures.
Red Hat Lightspeed uses YARA to evaluate the system for the presence of malware.
This requires additional setup above and beyond Red Hat Lightspeed registration.
Setting up Malware Detection
-
Log into your host using the terminal window on the right side of your showroom. The Terminal is logged into your bastion host - you will need to log into
node-{guid}-1.example.com.
ssh lab-user@node-{guid}-1.example.comIn your environment you would need to install the yara client. This is part of the appstream repository in RHEL 8 and 9.
In the lab this has already been done for you, but the command is as follows:
sudo dnf install yara -y| If you run the command above it won’t hurt anything - you will just receive a message stating that there is "Nothing to do" since the package is already installed. |
-
Initiate yara by running the malware detection collector command:
sudo insights-client --collector malware-detectionSince Red Hat Lightspeed malware detection had never been run before on this system the malware detection service performed some setup including the creation of a config file.
You would normally need to edit the config file to make scans live, but we have already done this for you in the lab.
The Malware detection service is now set up.
Since this is a new system, there is nothing to find - yet.
Download the Malware Test Signature and evaluate for Malware
On your host you should be in your user’s home directory.
-
Run the
llcommand. You should not see any files listed in the directory.
We will go ahead and have this system generate a malware detection hit.
To do this we will use the eicar set of test files.
More information about eicar is available here if you would like to learn more: https://www.eicar.org/download-anti-malware-testfile/
This set of test files includes 4 different files that test the detection of malware in 4 different ways.
On your host we will use the curl command to copy the files from the eicar webpage onto your host.
-
Run the following command:
curl -O "https://secure.eicar.org/{eicar.com,eicar.com.txt,eicar_com.zip,eicarcom2.zip}"-
Run the
llcommand again.
You should see the 4 eicar files in your directory.
Each file contains the same text which simulates a malware signature: -
Lets run the malware detection scan on your system.
| This may take several minutes to complete. |
sudo insights-client --collector malware-detectionIn the output you should see:
Scanning files in /home ...
Matched rule XFTI_EICAR_AV_Test in file /home/lab-user/eicar.com
Matched rule XFTI_EICAR_AV_Test in file /home/lab-user/eicar.com.txt
Matched rule XFTI_EICAR_AV_Test in file /home/lab-user/eicar_com.zip
Matched rule XFTI_EICAR_AV_Test in file /home/lab-user/eicar_com2.zipThat is yara finding the malware signature from eicar in each of the four files. Now you can see malware detected inside of Red Hat Lightspeed.
| Wait until the command is completely finished running and you are returned to the terminal prompt before continuing. |
Reviewing Malware Detection Results
-
Return to the Hybrid Cloud Console.
-
On the left hand navigation bar go to
Security → Malware → Signatures
Here you should see a big red exclamation mark telling you that we have matched a malware signature.
If there were no malware matches you would see a green checkmark. Due to the shared environment with multiple people taking this lab it is unlikely you will see the green checkmark today.
Looking next to the exclamation mark you will see the number of matched signatures as well as the number of enabled and disabled signatures.
Malware detection signatures can be disabled in the event that a false positive is detected, but your user account in this lab does not have the permissions to enable or disable signatures. -
Scroll down the page and you will see the matched signature -
XFTI_EICAR_AV_Test -
Click on
XFTI_EICAR_AV_Test. You will see the details of the signature and which systems have matched this malware. -
Locate your system.
Reminder: your system name is:node-{guid}-1.example.com
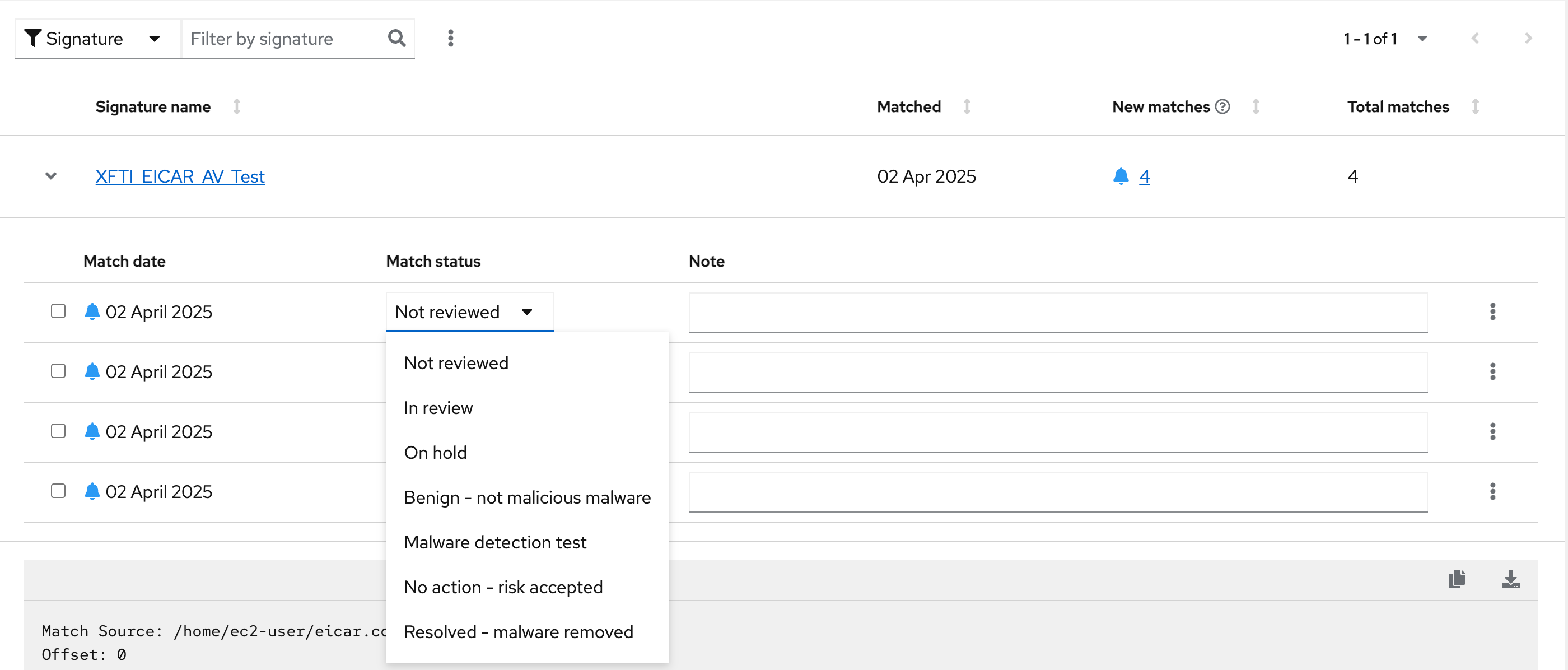
You should notice that you have the date of the last match and the total number of matches. The total number of matches should be4assuming that you only ran the commands as described in the exercise - that is because the eicar package included 4 test files - one match for each of the files. -
Click on your system’s name to view the details.
Here you can see the details of the match. Click the arrow to the left of the Malware signature match to view more information.
For each match you can set the match status.
Your user in the lab doesn’t have access to these options to provide a better experience for all users, but the options are:
-
Not Reviewed
-
In review
-
On hold
-
Benign - not malicious malware
-
Malware detection test
-
No action - risk accepted
-
Resolved - malware removed
If you scroll down the page you can download the details as a text file or copy it to your clipboard for the purposes of sending these details to your security team.
As you look through the output you should see 4 different “Match Source” entries - one for each of the eicar files that you put onto the system.
The Malware detection service does not include any remediation. This is because each business likely has their own policies and procedures on how malware on systems should be handled once detected.
This module is complete.