Module 3: Integrating and Observing Virtual Machines in OpenShift Service Mesh
In this module we are going to introduce Red Hat OpenShift Service Mesh and explore the added features, to elevate the experience of operating and monitoring Virtual Machines(VMs) as first class citizens in a cloud native world.
Objectives
-
Introducing OpenShift Service Mesh
-
Integrate VMs with OpenShift Service Mesh for advanced networking
-
Implement traffic management rules and review new observability features through OSSM
About OpenShift Service Mesh
Red Hat OpenShift Service Mesh is an integrated service mesh solution based on Istio, Kiali, and Jaeger, designed to simplify microservices communication, security, and observability in OpenShift environments. It provides a uniform way to manage service-to-service interactions, including traffic control, security policies, and monitoring.
| OpenShift Service Mesh is an add-on service that can be installed through an operator. |
Even though OpenShift Service Mesh is primarily designed for containerized workloads, it also supports VMs by integrating them into the mesh. Key benefits for VMs include:
-
Consistent Networking & Security – VMs can securely communicate with containerized workloads using mTLS encryption and access policies.
-
Unified Observability – VMs gain visibility through tracing (Jaeger), monitoring (Prometheus, Grafana), and service topology visualization (Kiali).
-
Traffic Management – Enables intelligent routing, load balancing, and failover between VMs and microservices.
-
Gradual Migration – Allows a hybrid approach, where legacy VMs can coexist and gradually transition into a containerized environment.
-
Policy Enforcement – Ensures compliance by applying service-level access control and security policies uniformly across VMs and containers.
| The following section provide additional information on the Service Mesh Architecture. Feel free to skip the following section to save time and come back later if needed. |
Informational Section: OpenShift Service Mesh Architecture
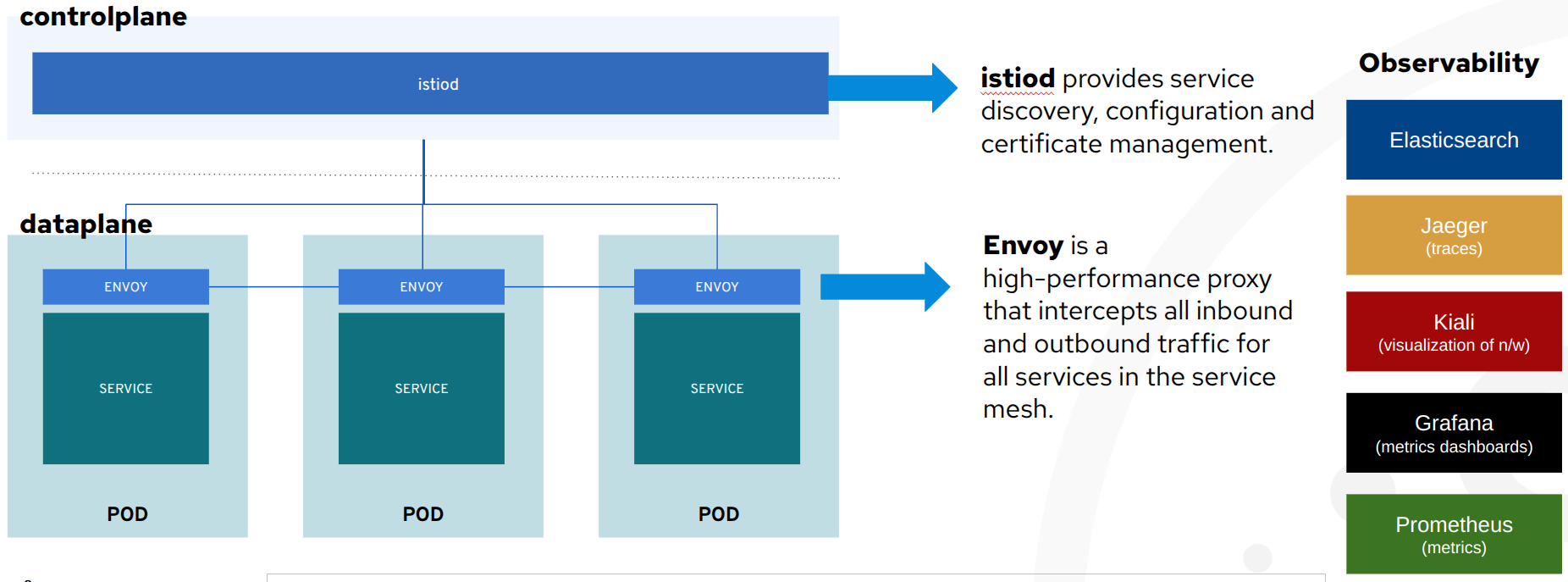
OpenShift Service Mesh, delivered as part of the platform, adds the above cross-cutting application capabilities through the following components:
-
istiod: applies all defined policies (encryption, authorization, traffic management, observability) in the network of VMs and containers included in the mesh.
-
envoy: a sidecar container, of a VM or containerized workload, with the ability to receive and apply the policies effectively making a VM part of the mesh. The envoy sits side-by-side to a VM (see the image above) and intercepts all requests coming in and out of it.
-
Kiali: visualises through a UI what is configured in the mesh, the network of included applications, the traffic througput and latency, the security utilised, the issues that may occur in the configurations or netwrork, the logs and a host of other features that the mesh offers.
-
The rest of the observbility components (as seen in the image above) contain parts of what
kialivisualises for a deeper inspection:-
Prometheuscollects the metrics emitted by theenvoyof each container/VM in the mesh, -
Jaegercollects traces of each container/VM in the mesh and draws a path (span) of the microservices a request traversed showing the time the request spent in each microservice and success/failure state, -
Grafanaprovides additional dashboards for the operators and business analysts to review on performance, request throughput/latency, success/failures etc.
-
-
Gateways: one or more
ingress gatewayinstances support traffic flow into service mesh from the outside. This is required since the mesh comes withnetwork policiesthat disable direct access to VMs/containers in the mesh. Also anegress gatewayrespectively can control outgoing traffic from the mesh to external services.
| The administrators of the cluster you will be using have already done the setup of Service Mesh so lets see how easy it is to enable a a VM to take advantage of these new capabilities. |