Declarative Management of VMs with OpenShift GitOps
All assets for this module are in the folder lab-5. Please change the directory into this folder.
|
cd $HOME/virt-ossm-workspace/lab-5In this module we want to deploy everything declaratively and let it be managed by OpenShift GitOps.
You’ll notice that three parts of the application, the travel-portal and travel-agency as well as the service mesh components are already managed by OpenShift GitOps.
|
We will be using a helm-chart to provide the Kubernetes and service mesh manifests for the missing travel-control domain.
But first, let’s explore what is already managed by OpenShift GitOps.
Task 1: Explore the ArgoCD Dashboard and the existing Argo applications
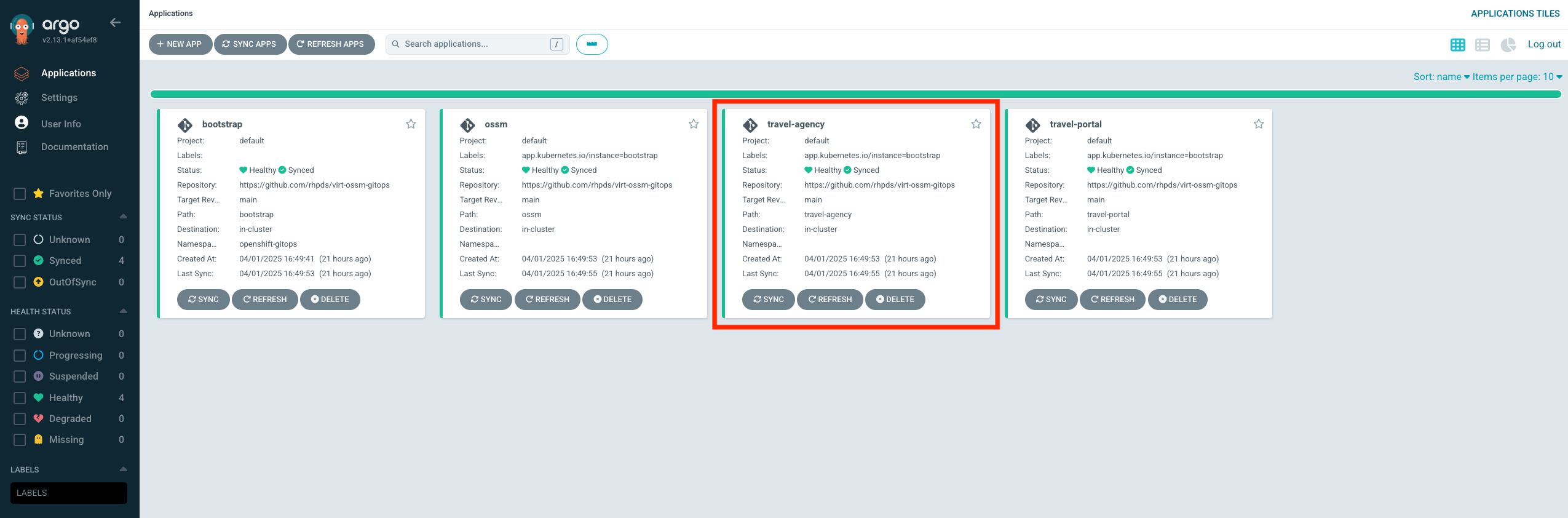
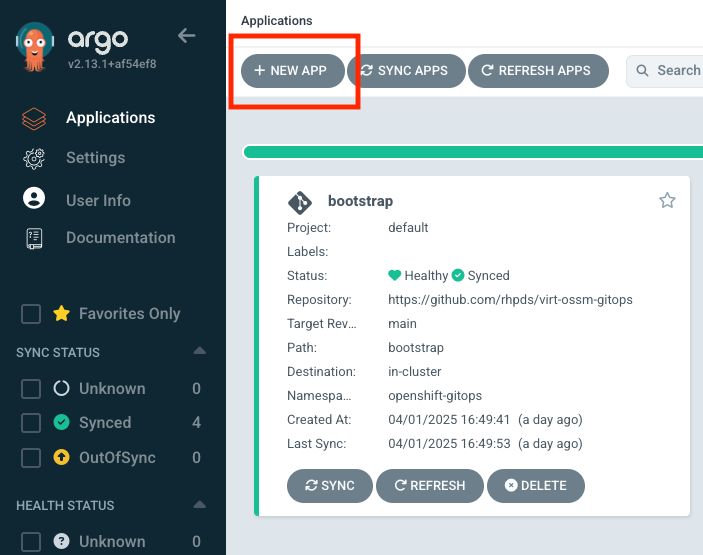
Welcome to the Argo Dashboard.
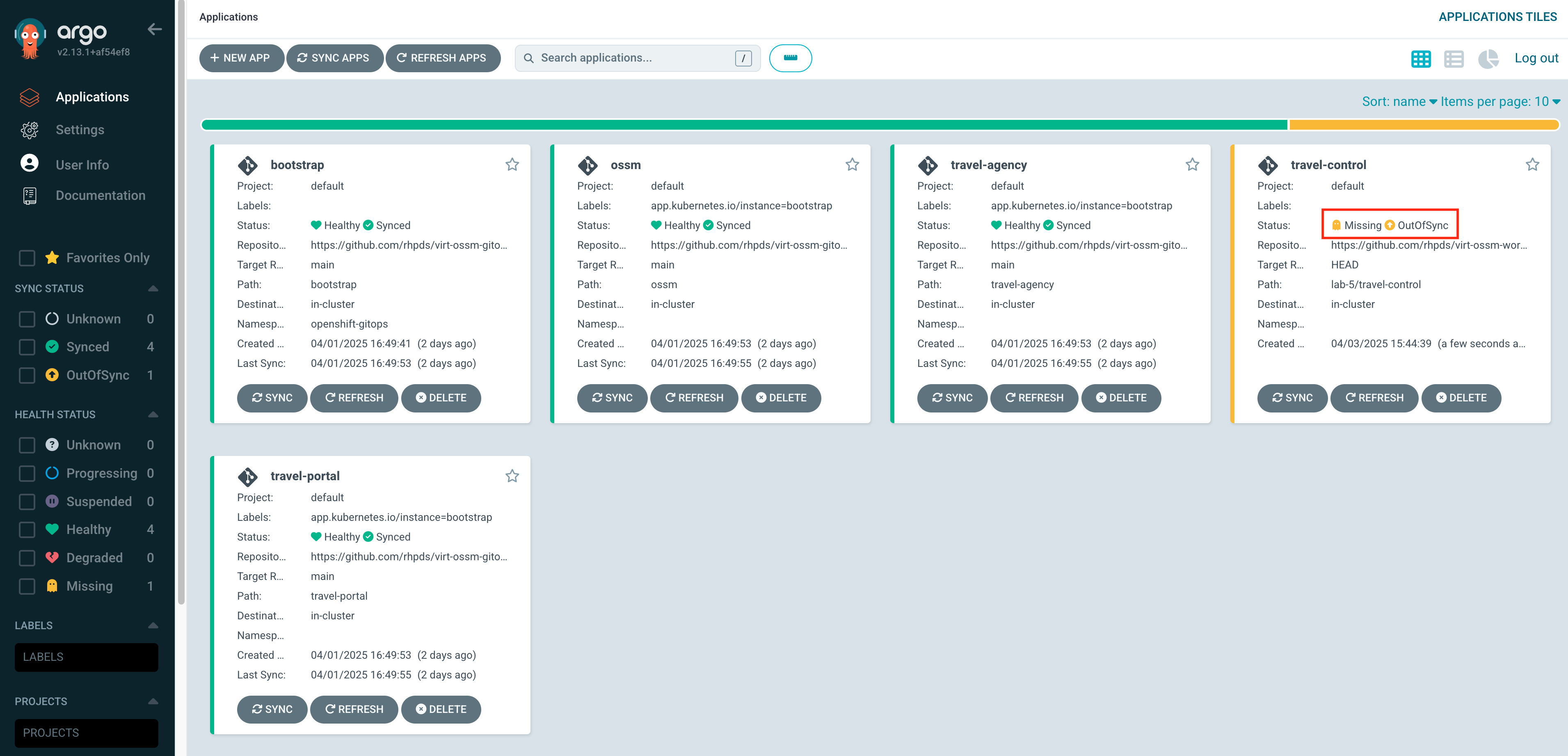
You see 4 Argo applications running and being managed by OpenShift GitOps. (You can ignore the bootstrap application)
An Argo CD application is a Kubernetes resource that defines and manages the deployment of workloads based on a Git repository. It continuously syncs the desired application state from Git to the cluster, ensuring consistency and enabling automated rollbacks if deviations occur.
You also notice the Sync status and the Health for each application:
Sync status - Whether or not the live state matches the target state. Is the deployed application the same as Git says it should be?
Health - The health of the application, is it running correctly? Can it serve requests?
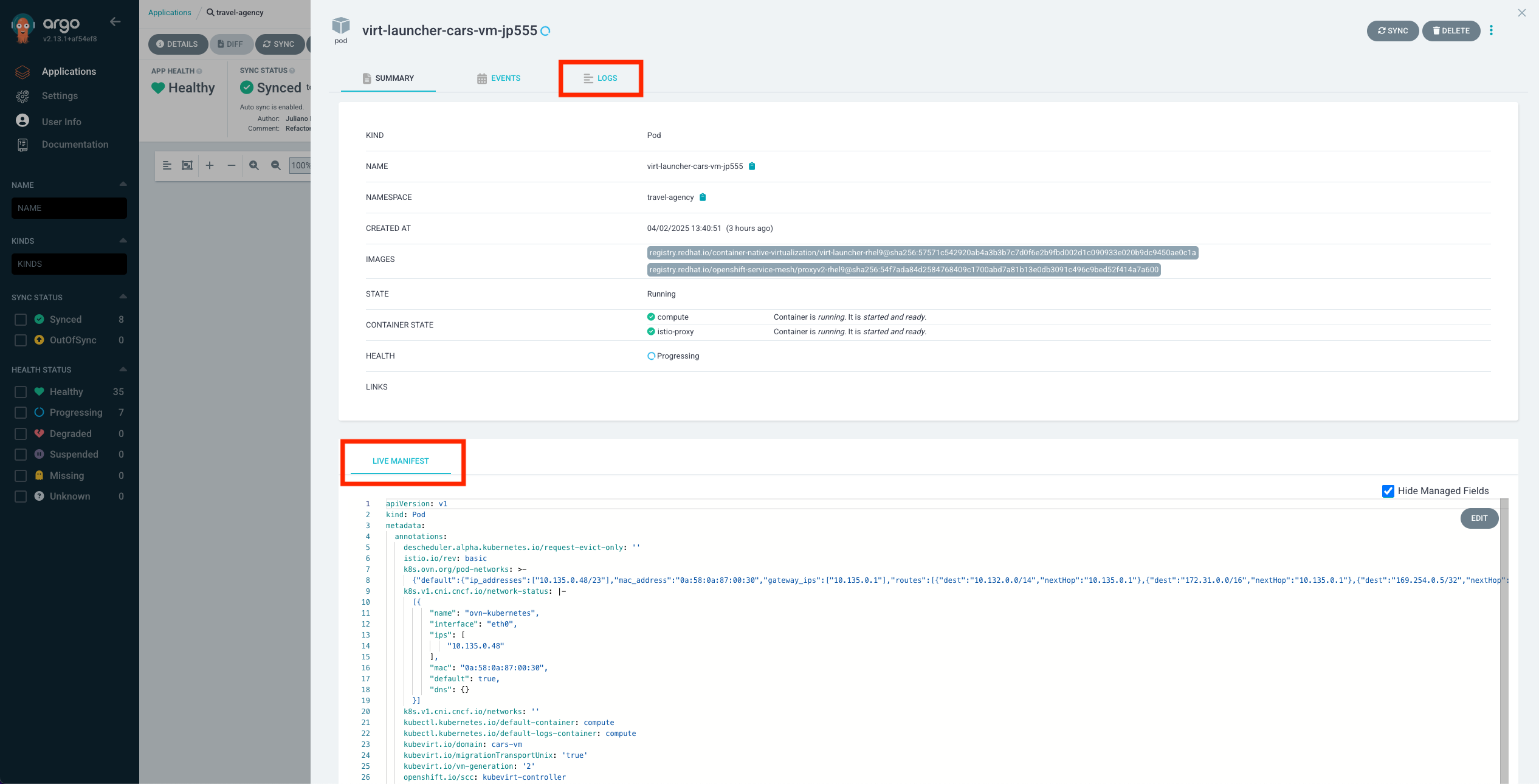
Now click on the travel-agency application.
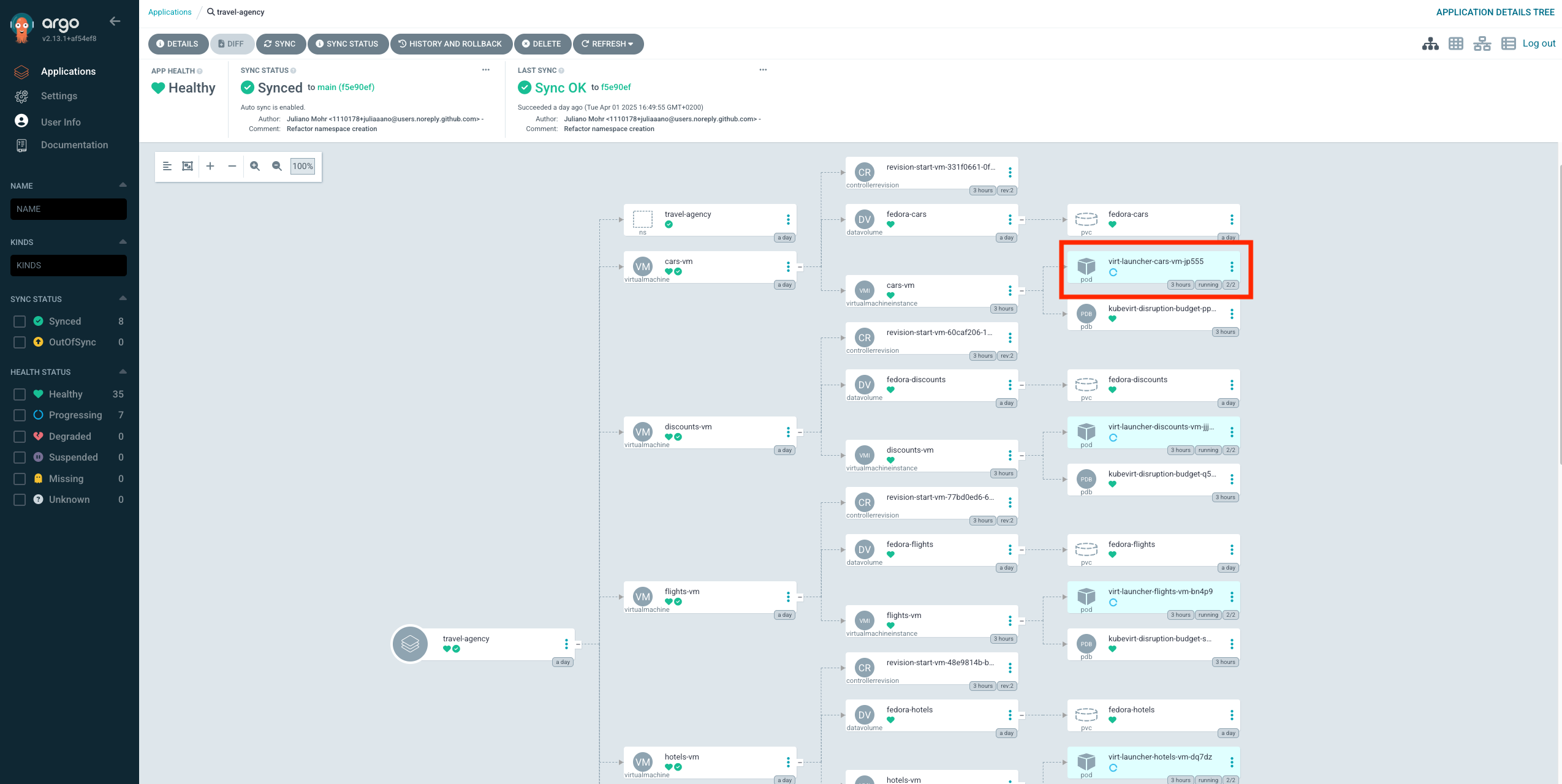
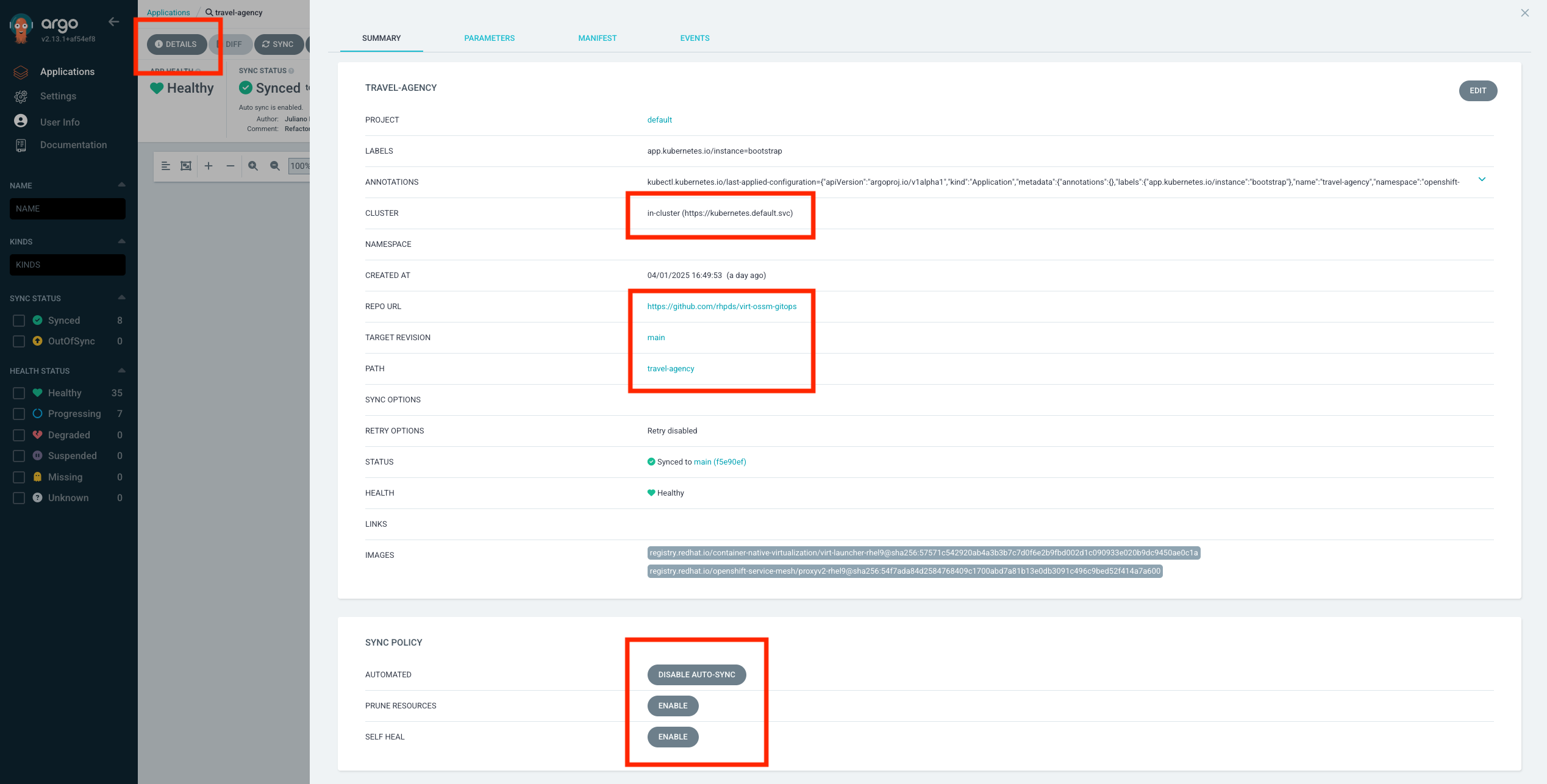
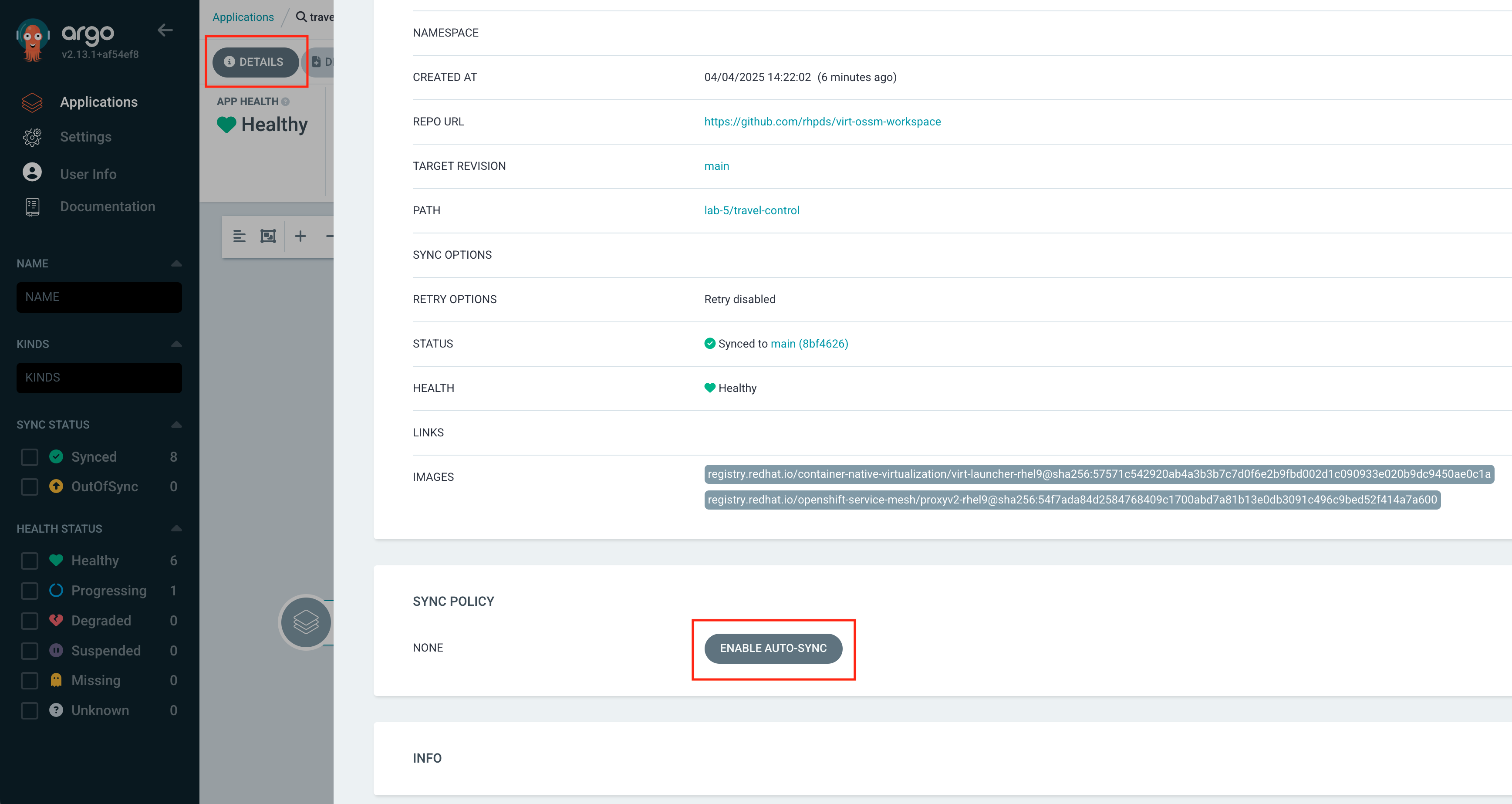
Back in the overview click on DETAILS at the top.
This gives you an overview of the configuration for this argo application, like the source git repository, the target cluster, status and health, as well as the configured
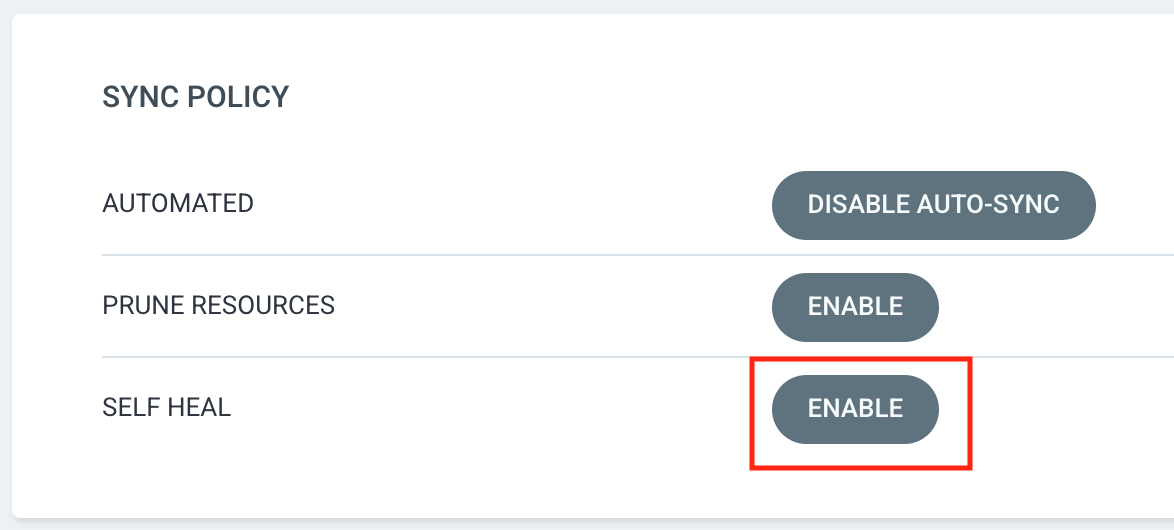
Sync Policy:
-
Automated Sync – Automatically applies changes from Git to the cluster when updates are detected, without manual intervention.
-
Prune Resources – Deletes resources from the cluster if they are removed from the Git repository, preventing orphaned resources.
-
Self-Heal – Continuously monitors and corrects drift by reverting manual changes in the cluster to match the desired state from Git.
Close the window and click on Applications in the left menu of the Argo Dashboard.
Task 2: Create an Argo application for travel-control
Imagine a DevOps engineer accidentally deletes the travel-control namespace that contains critical applications for the Travel Agency company. Without Argo CD, this would require manual intervention to restore the namespace and redeploy the applications, leading to downtime.
Exactly, what we do right now!
oc delete project travel-control| With Argo CD and Self-Heal enabled, the system would detect the deletion and automatically recreates the namespace and all its resources from the Git repository. This ensures minimal disruption and maintains the desired state without manual effort. |
This makes Argo CD a great fit for teams that need automated recovery, drift correction, and continuous deployment in OpenShift.
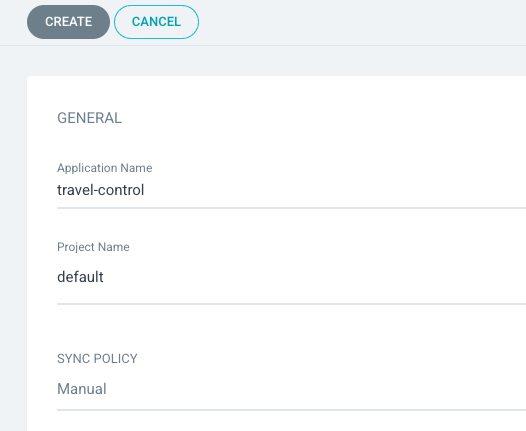
Now let us create an argo app for the travel-control component.
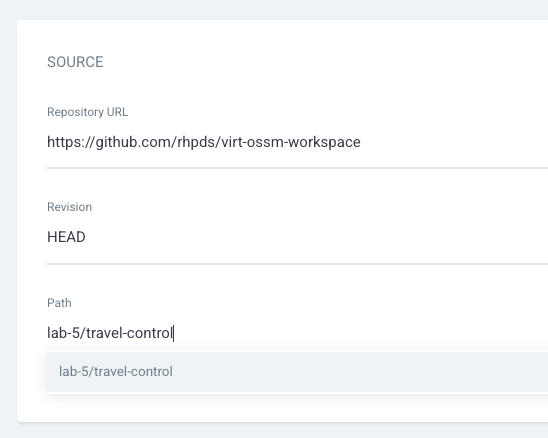
Connect the https://github.com/rhpds/virt-ossm-workspace repo to Argo CD by setting repository url to the github repo url, leave revision as HEAD, and set the path to lab-5/travel-control:
We have already provided all necessary Kubernetes manifests in this repository and path. Feel free to explore this Helm Chart if you like.
|
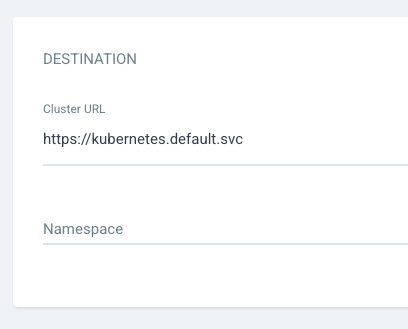
For Destination, set cluster URL to https://kubernetes.default.svc (or in-cluster for cluster name) and leave the namespace empty:
In the last step we test if the whole solution is working correctly, by opening the Business Dashboard of the Booking Application again.
Task 3: Validate Argo CD Self-Healing
To test Argo CD’s self-healing capability, you can manually delete a Kubernetes resource managed by Argo CD. With Automated Sync and Self-Heal enabled, Argo CD will detect the drift from the desired Git state and automatically recreate the deleted resource, confirming that self-healing is working as expected.
Now we are going to delete all content from the travel-control namespace. Execute the following command in the terminal on your right hand side:
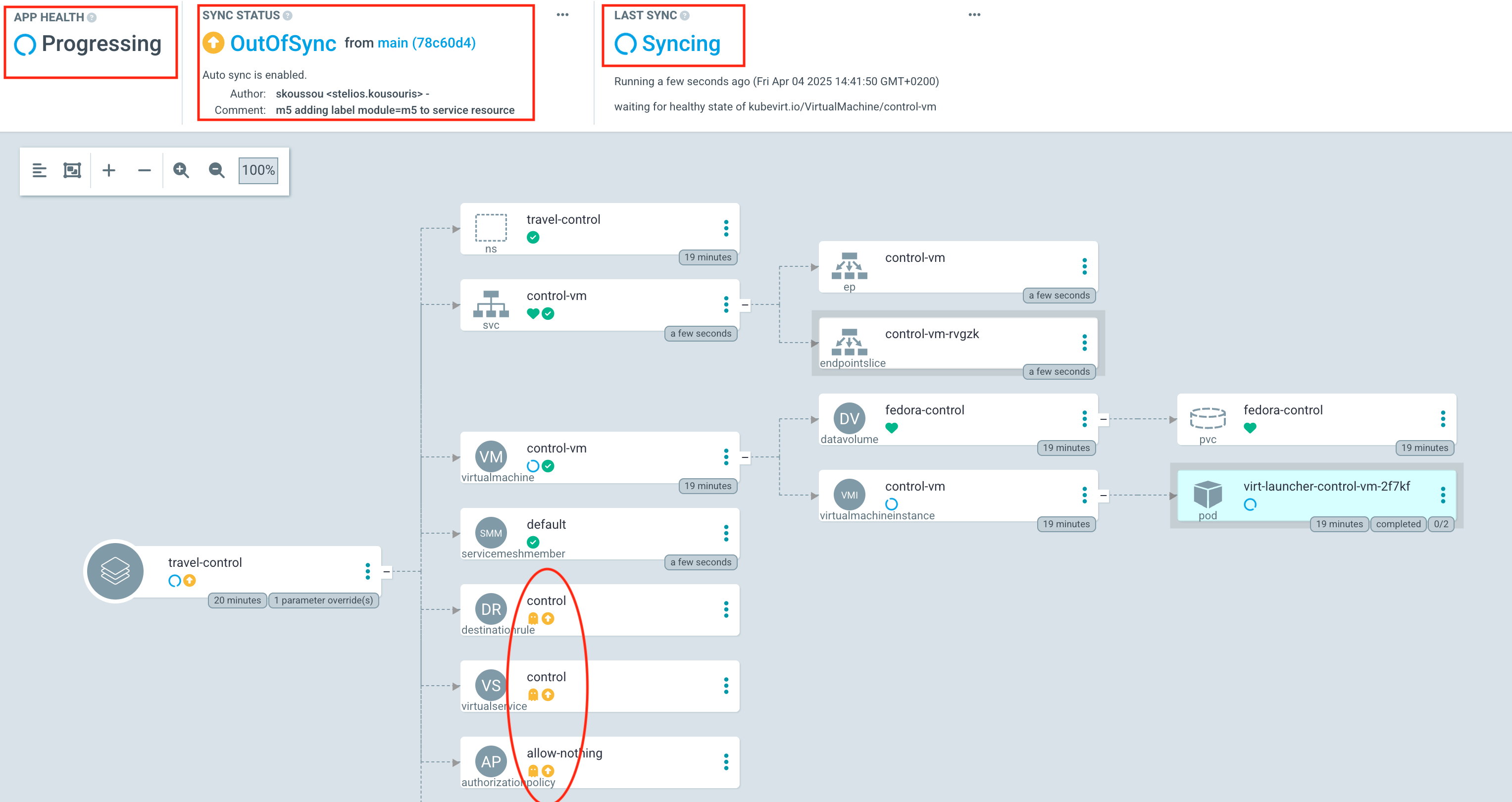
oc delete AuthorizationPolicy,DestinationRule,Route,Service,smm,VirtualMachine,VirtualService -l module=m5 -n travel-controlThe Argo CD dashboard will briefly show:
-
Application status as "OutOfSync" – indicating that the live cluster state no longer matches the Git source.
-
The deleted resource will disappear from the resource tree temporarily.
-
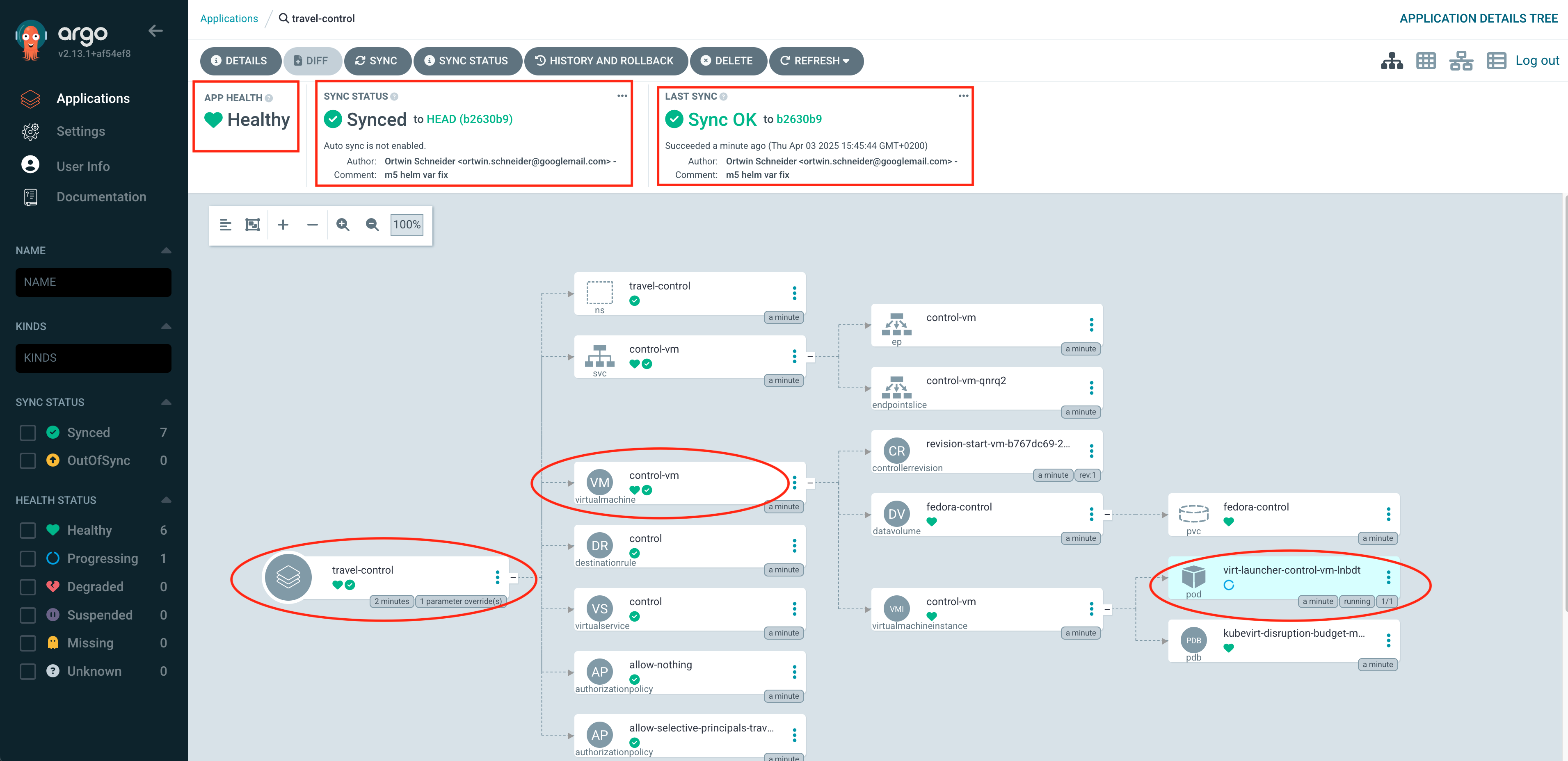
Within moments, Argo CD will auto-sync, and the deleted resource will reappear, restoring the desired state.
-
The status will return to "Synced" and "Healthy", confirming self-healing has taken place.
Congratulations!! You helped the Travel Agency company to operate their whole solution now through GitOps.