Notifications
Module Goals
-
Understanding how notification and alerting work in RHACS
-
Set up a notification alert to a Microsoft Teams channel
-
Set up a notification alert to a Slack channel
-
Configure policies to send alerts to both Teams and Slack
How Do Notifications and Alerts Work in RHACS
Red Hat Advanced Cluster Security for Kubernetes (RHACS) offers robust notification and alerting mechanisms to enhance the security and observability of Kubernetes environments.
Notification and Alerting Mechanisms
Policy Violations
RHACS uses a set of pre-defined and custom policies to monitor the cluster for security violations. These policies can cover a wide range of security aspects including image vulnerabilities, misconfigurations, runtime behaviors, and compliance checks. When a policy is violated, RHACS generates a violation event. These events are the primary triggers for notifications and alerts.
Alert Configurations
RHACS supports integrations with various notification and alerting systems such as Slack, Microsoft Teams, email, PagerDuty, Splunk, and more. For systems not directly supported, custom webhooks can be configured to send alerts to any endpoint that can process HTTP POST requests.
Setting Up Notifications
Administrators can configure notification channels through the RHACS console. This involves providing the necessary credentials and endpoints for the chosen notification service. These notifications can be scoped to specific policies, allowing for granular control over which violations generate alerts and where those alerts are sent.
Alert Management
Policies can be assigned different severity levels (Low, Medium, High, Critical). Alerts can be configured to trigger based on the severity level of the violation. Depending on the integration, alerts can be routed to different teams or systems. For example, critical violations can be sent to on-call engineers via PagerDuty, while lower-severity alerts might be sent to a Slack channel for informational purposes.
Runtime Alerts
RHACS continuously monitors Kubernetes clusters for runtime anomalies. Alerts can be configured to trigger on suspicious activities such as unexpected network connections, process executions, or file system changes. By analyzing the runtime behavior of applications, RHACS can alert on deviations from known good states or behaviors.
Integrating Slack with RHACS
In this guide, we will show you how to integrate Red Hat Advanced Cluster Security (RHACS) with Slack by setting up an Incoming Webhook in Slack and configuring it in RHACS to receive security alerts.
Prerequisites
Before proceeding, ensure you have the following: - A Slack account and access to create a Slack app.
Steps for Setting Up the Slack Integration
Procedure
-
Visit the Slack API site: https://api.slack.com/apps?new_app=1 and log in with your Slack credentials.
-
Click MORE, then click Automations:
-
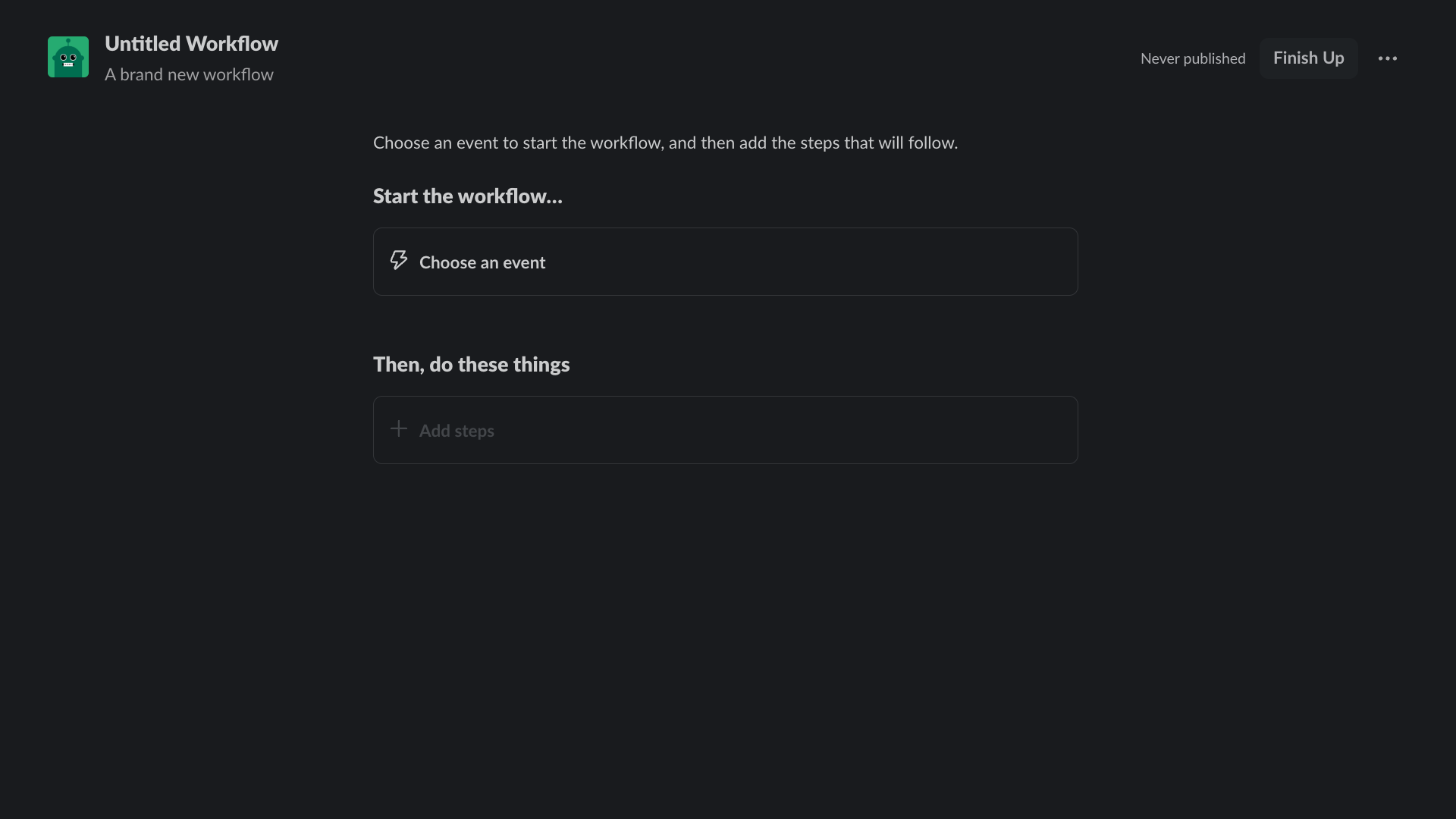
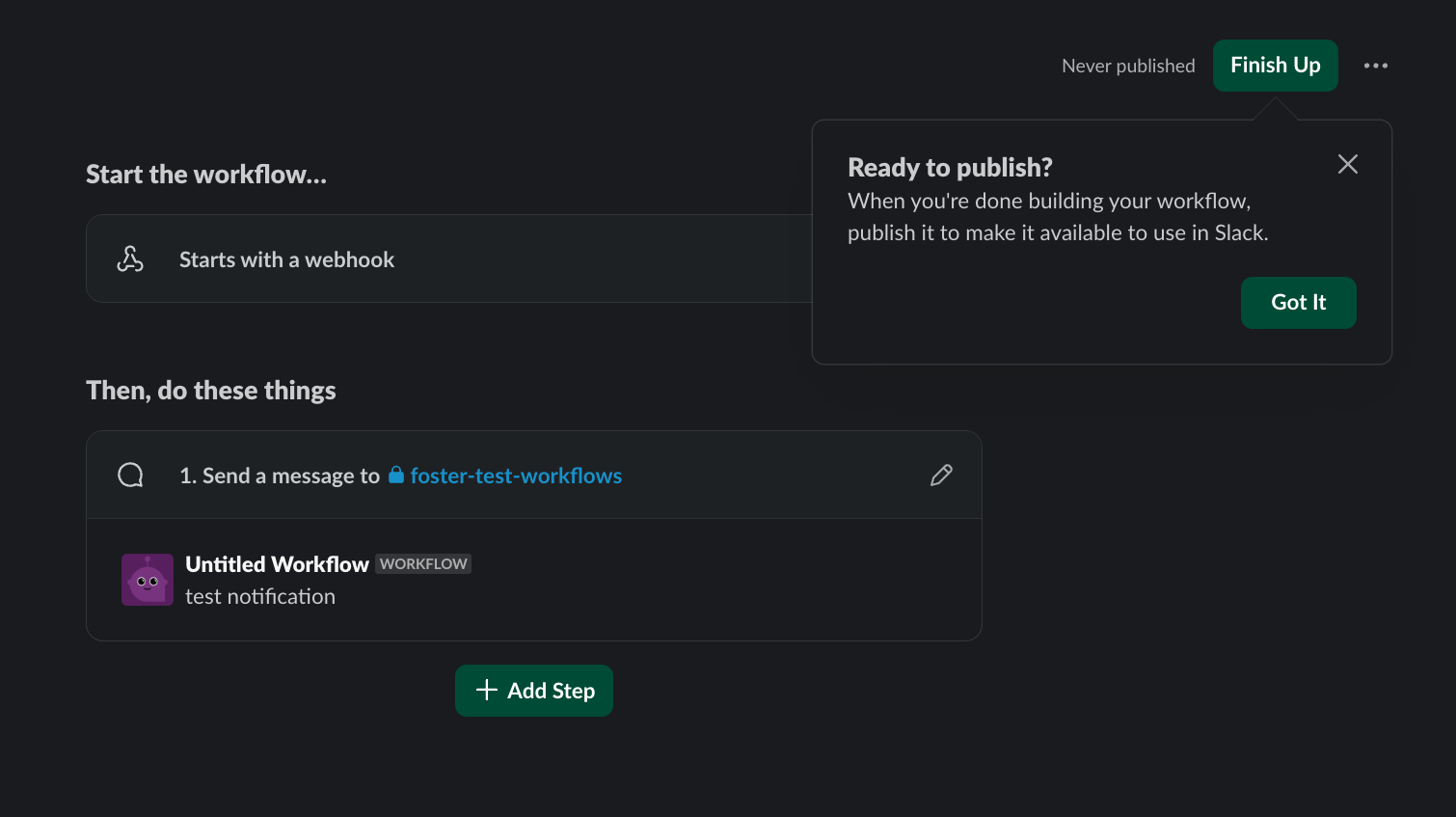
Select New Workflow at the top right of the page:
-
Select New Workflow at the top right of the page.
-
Click the workflow title and give it the following name: first-notification-workflow.
-
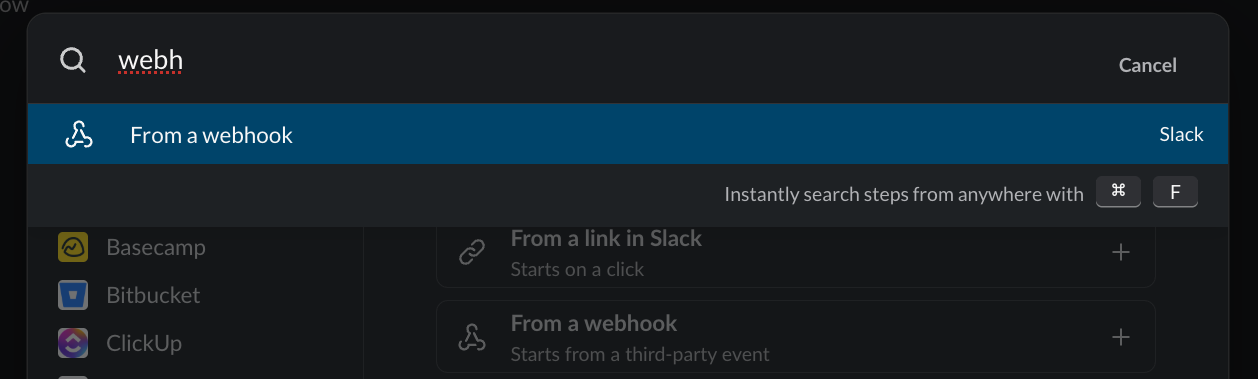
Search for webhook and select it:
-
Hit continue.
-
Select the Slack workspace where it will be used:
| You can add additional features like webhooks or bot users later, but for now, focus on setting up the Incoming Webhooks. |
-
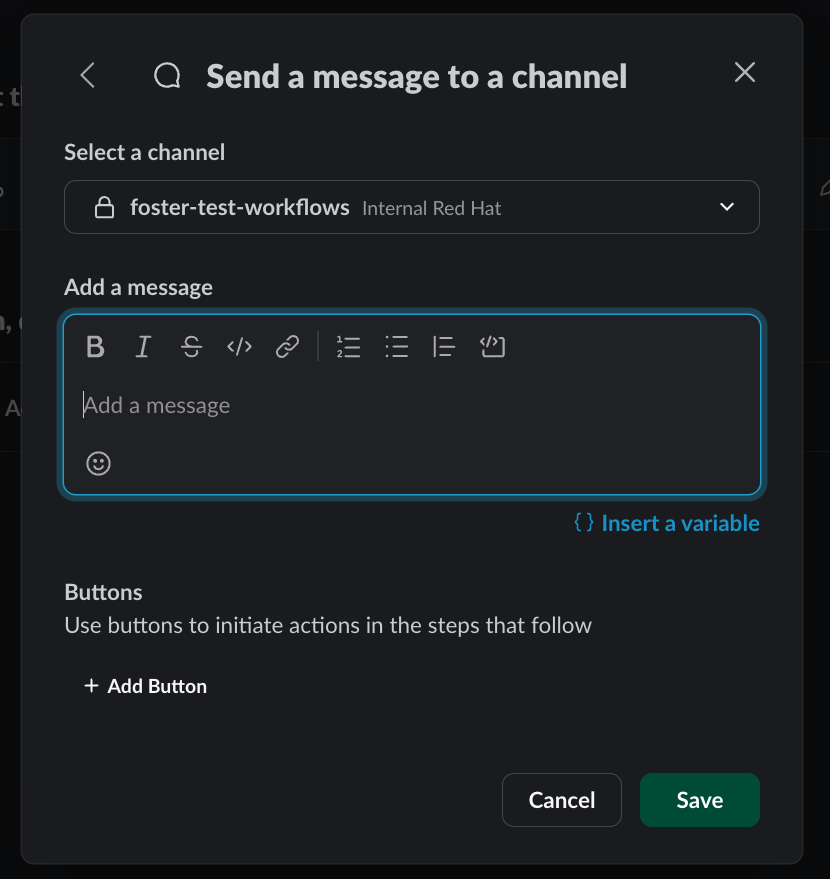
Add a test prompt and save it.
-
Then click Finish Up:
-
Scroll down to the Webhook URLs for Your Workspace section:
-
Next, copy the unique Webhook URL and navigate to the RHACS dashboard:
-
Log into the RHACS Console and navigate to Platform Configurations → Integrations:
-
Under Notifier Integrations, select Slack:
-
Click the New integration button to start the configuration:
-
Integration Name: Enter: slack-alerts
-
Webhook URL: Paste the Webhook URL you copied earlier from Slack.
-
Default Channel: This is typically auto-populated based on the Webhook URL, but verify or select the correct Slack channel.
-
-
Click Test to ensure the integration works correctly:
-
If successful, you will see the message "The test was successful".
References
-
[Slack API Documentation](https://api.slack.com/)
Next, we have to configure our policies to alert based on specific triggers.
Integrating Microsoft Teams with RHACS
In this guide, we will show you how to integrate Red Hat Advanced Cluster Security (RHACS) with Microsoft Teams by setting up an Incoming Webhook in Teams and configuring it in RHACS to receive security alerts.
Prerequisites
Before proceeding, ensure you have the following:
-
A Microsoft Teams account and access to create a Teams app.
-
Administrator permissions in your Microsoft Teams organization.
Steps for Setting Up the Microsoft Teams Integration
Procedure
-
Navigate to the Microsoft Teams web app or desktop application and log in with your Microsoft credentials:
-
Go to the channel where you want to receive the notifications:
-
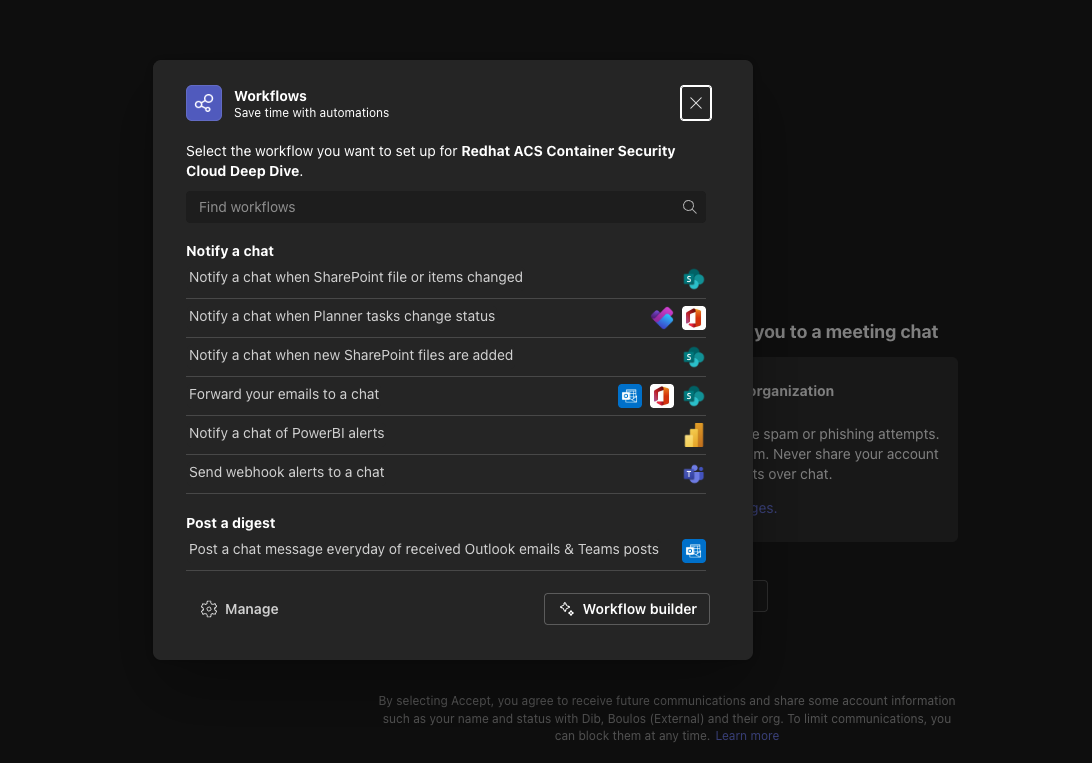
Click the More options (three dots) next to the channel name and select Workflows:
-
In the Workflows dialog, click send webhook alerts to chat:
-
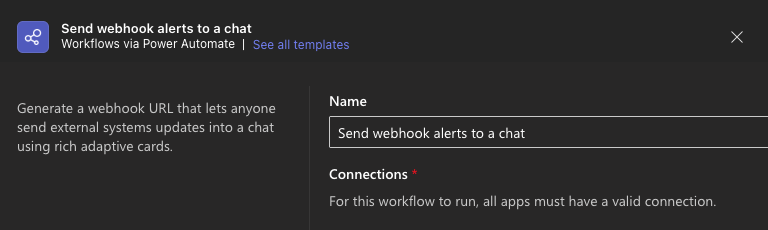
Fill in the webhook details:
-
Name: Enter: RHACS Security Alerts
-
-
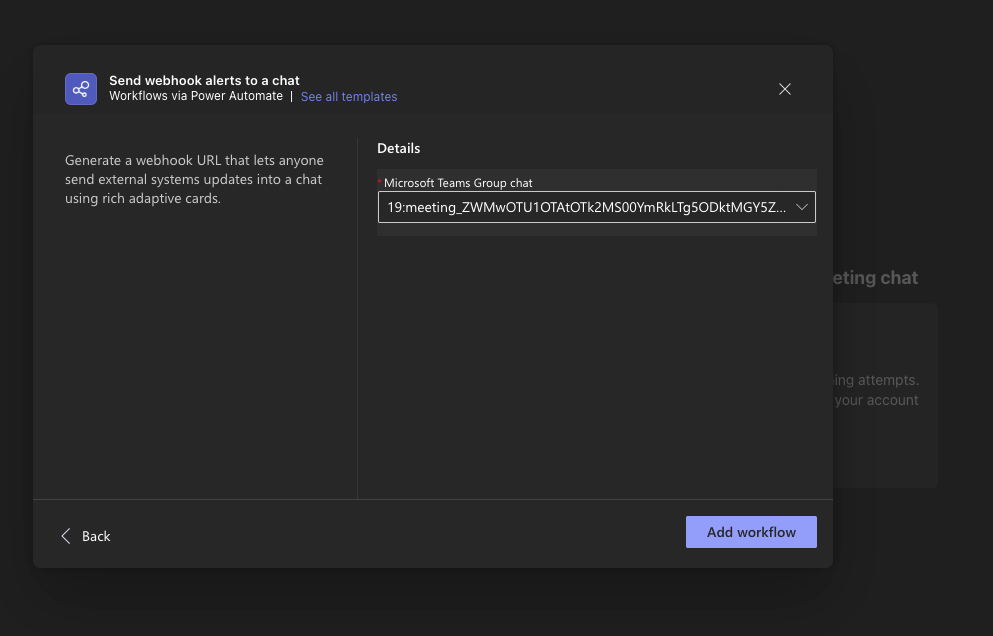
Click add workflow:
-
Copy the Webhook URL that is generated. You will need this for the RHACS configuration
-
Navigate to the RHACS Console and log in
-
Go to Platform Configurations → Integrations
-
Under Notifier Integrations, select Microsoft Teams
-
Click the New integration button to start the configuration
-
Configure the Teams integration.
-
Integration Name: Enter: teams-alerts
-
Webhook URL: Paste the Webhook URL you copied earlier from Teams.
-
-
Click Test to ensure the integration works correctly
-
If successful, you will see the message "The test was successful".
-
Click Save
References
-
[Microsoft Teams Webhook Documentation](https://docs.microsoft.com/en-us/microsoftteams/platform/webhooks-and-connectors/how-to/add-incoming-webhook)
Next, we have to configure our policies to alert based on specific triggers.
Configure Notifications
Balancing security alerting in a team is crucial to ensure that the team is responsive to genuine threats while minimizing alert fatigue. RHACS enables this by letting you configure your alert channels and attach them to the policies you care about.
Let’s test this out. You will use the runtime enforcement policy that was used in the previous module.
Procedure
-
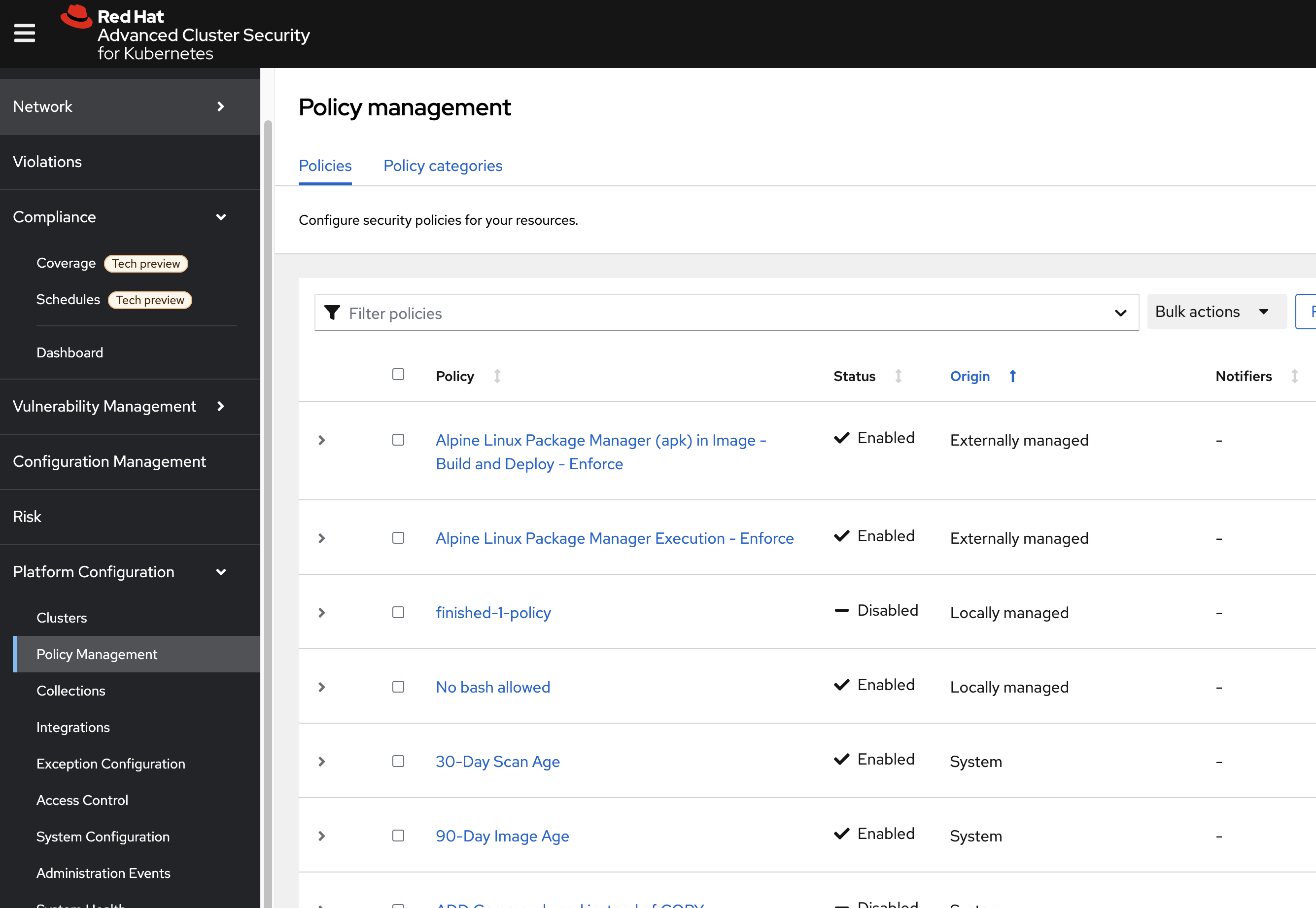
On the left-hand side of the application, click the Platform Configuration tab and select Policy Management:
-
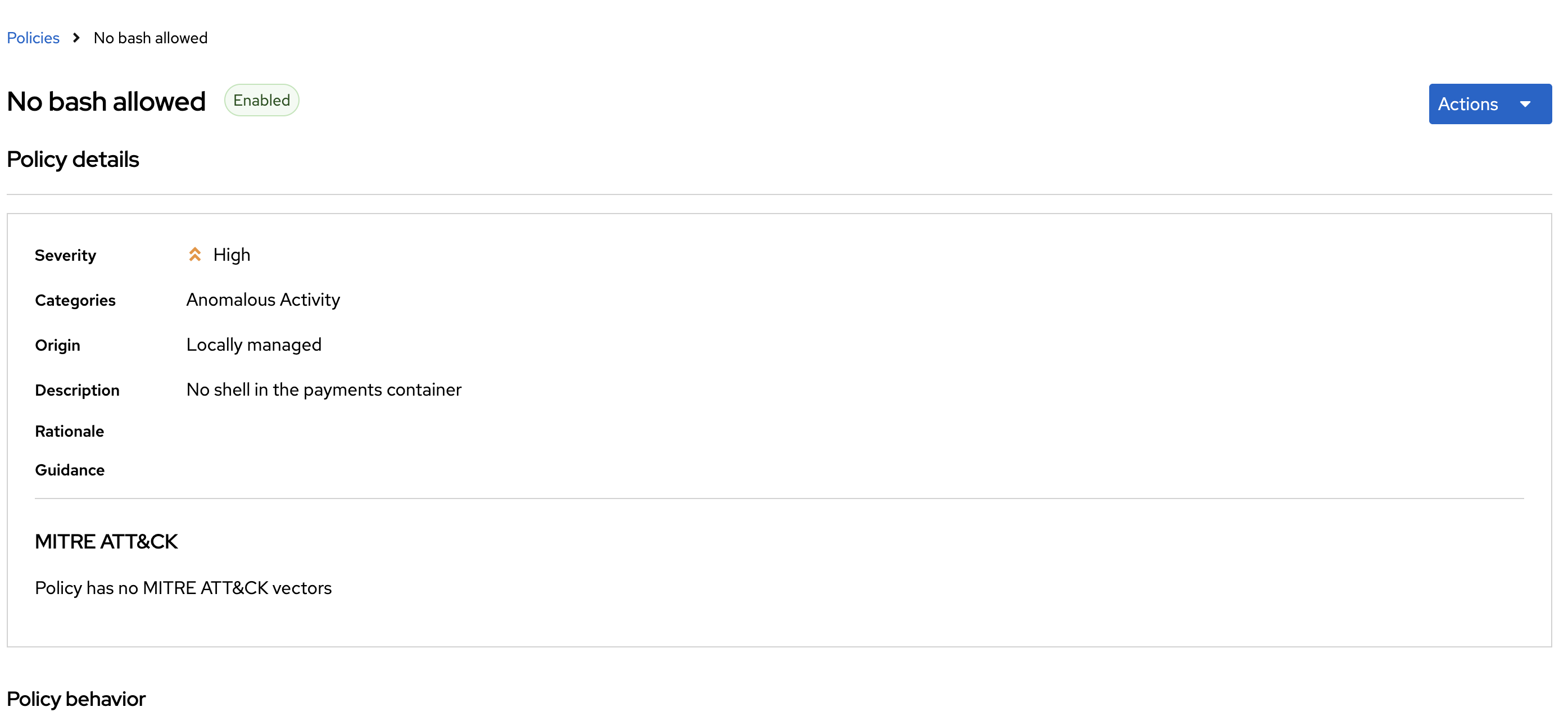
Filter through the policies to find No bash allowed or use the search bar to select Policy:
-
Once you have found the policy No bash allowed, click to edit the policy:
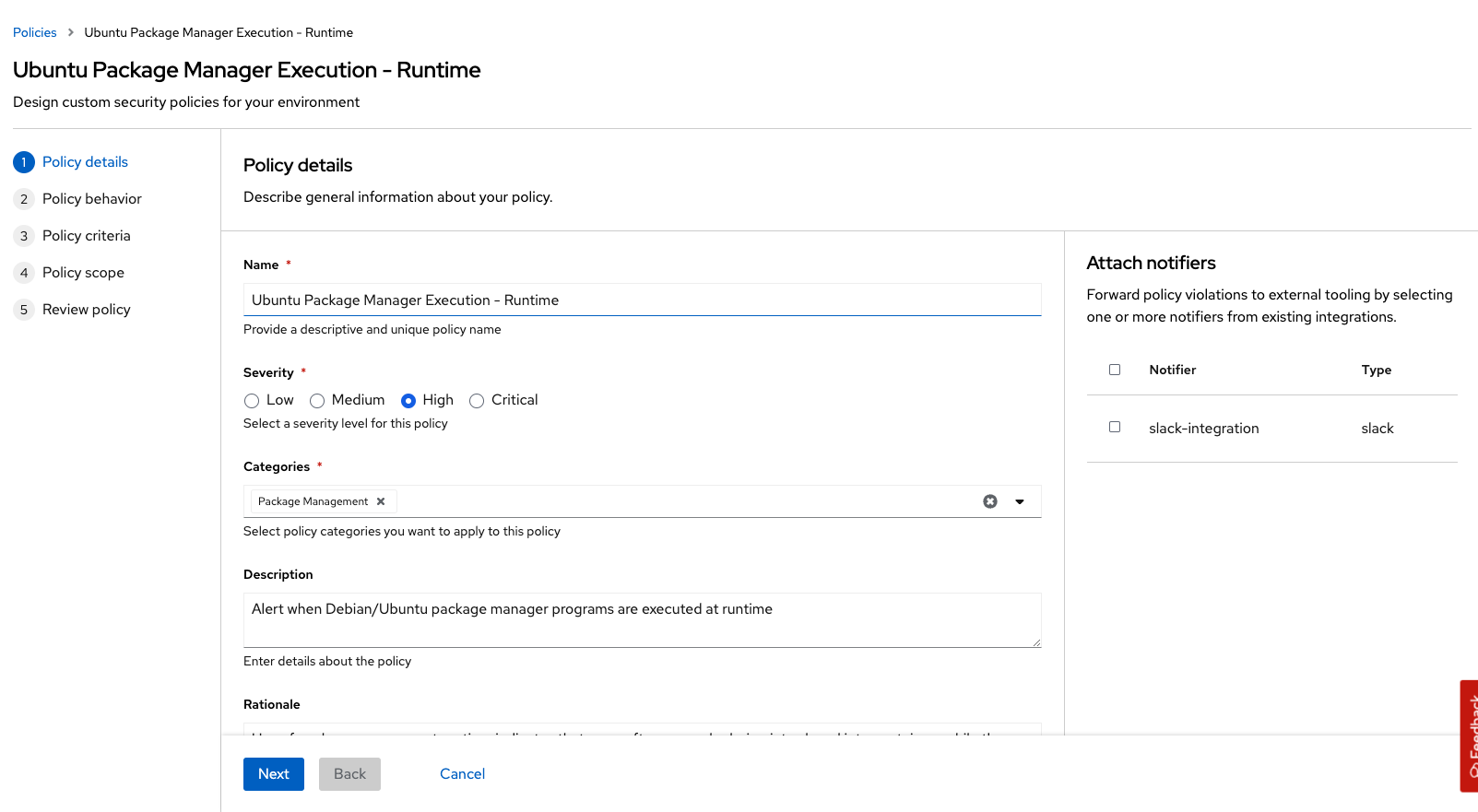
-
Go to Policy behavior - actions. There should be your slack-alerts and teams-alerts notifier options available:
-
Click the desired notifier(s) and save the policy:
| Run the following command if you have not created the policy in the earlier module: |
cat <<EOF | oc apply -n stackrox -f -
apiVersion: config.stackrox.io/v1alpha1
kind: SecurityPolicy
metadata:
name: no-bash-allowed
labels:
app.kubernetes.io/name: anomalous-activity-policy
app.kubernetes.io/part-of: security-policies
spec:
policyName: No bash allowed
description: 'Privilege escalation technique'
rationale: ''
remediation: Uninstall during container build
disabled: false
categories:
- Anomalous Activity
lifecycleStages:
- RUNTIME
eventSource: DEPLOYMENT_EVENT
exclusions: []
scope:
- cluster: ''
namespace: payments
label: null
severity: HIGH_SEVERITY
enforcementActions: []
SORTName: ''
SORTLifecycleStage: ''
SORTEnforcement: false
policyVersion: '1.1'
policySections:
- sectionName: ''
policyGroups:
- fieldName: Process Name
booleanOperator: OR
negate: false
values:
- value: bash
mitreAttackVectors: []
criteriaLocked: false
mitreVectorsLocked: false
isDefault: false
EOF-
Run the following command in the terminal:
POD=$(oc get pod -n payments -l app=visa-processor -o jsonpath="{.items[0].metadata.name}")
oc exec $POD -n payments -i --tty -- /bin/bash[demo-user@bastion ~]$ POD=$(oc get pod -l app=ctf-web-to-system -o jsonpath="{.items[0].metadata.name}")
oc exec $POD -i --tty -- /bin/bash
tomcat@visa-processor-9bfcf46f7-cwtjb:/usr/local/tomcat$| If you see tomcat@visa-processor…, you’ve confirmed you have a shell and access to the visa-processor application. |
-
Lastly, review your Slack and/or Teams channel for the alert:
Congrats!