RHACS Log4Shell Vulnerability Quick Lab
This lab shows how to block workloads with Log4Shell vulnerabilities using Red Hat Advanced Cluster Security (RHACS).
-
Block the vulnerable deployment of a log4shell application
-
Craft a policy to block the deployment of any application that uses log4shell
-
Verify the policy in the RHACS console
1. Clean Up Environment
Run these commands to reset your environment:
if oc get project log4shell &>/dev/null; then
oc delete project log4shell
else
echo "Project 'log4shell' already cleaned up."
fi
if [ -f ~/deploy.yaml ]; then
rm -f ~/deploy.yaml
else
echo "'~/deploy.yaml' already cleaned up."
fi
POL_ID=$(curl -k -H "Authorization: Bearer $ROX_API_TOKEN" "https://$ROX_CENTRAL_ADDRESS/v1/policies" | jq -r '.policies[] | select(.isDefault|not) | .id')
if [ -n "$POL_ID" ] && [ "$POL_ID" != "null" ]; then
curl -k -X DELETE -H "Authorization: Bearer $ROX_API_TOKEN" "https://$ROX_CENTRAL_ADDRESS/v1/policies/$POL_ID"
else
echo "Policy already cleaned up."
fi2. Deploy Vulnerable Application
Awesome! You’re ready to go. Now, create a new project and deploy the vulnerable Log4Shell app:
oc new-project log4shell
cat << EOF > ~/deploy.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: log4shell
namespace: log4shell
spec:
replicas: 1
selector:
matchLabels:
deployment: log4shell
template:
metadata:
labels:
deployment: log4shell
spec:
containers:
- name: log4shell
image: quay.io/rhacs-misc/log4shell:1.0
imagePullPolicy: IfNotPresent
ports:
- containerPort: 8080
protocol: TCP
restartPolicy: Always
EOF
oc create -f ~/deploy.yamlCheck the pod status:
oc get pods -l deployment=log4shell -n log4shell| You can add -w to the command to watch the pod status. |
[lab-user@bastion ~]$ oc get pods -l deployment=log4shell -n log4shell
NAME READY STATUS RESTARTS AGE
log4shell-6454cfb8c9-whskt 0/1 ContainerCreating 0 9s
log4shell-6454cfb8c9-whskt 1/1 Running 0 12s3. Verify Vulnerability
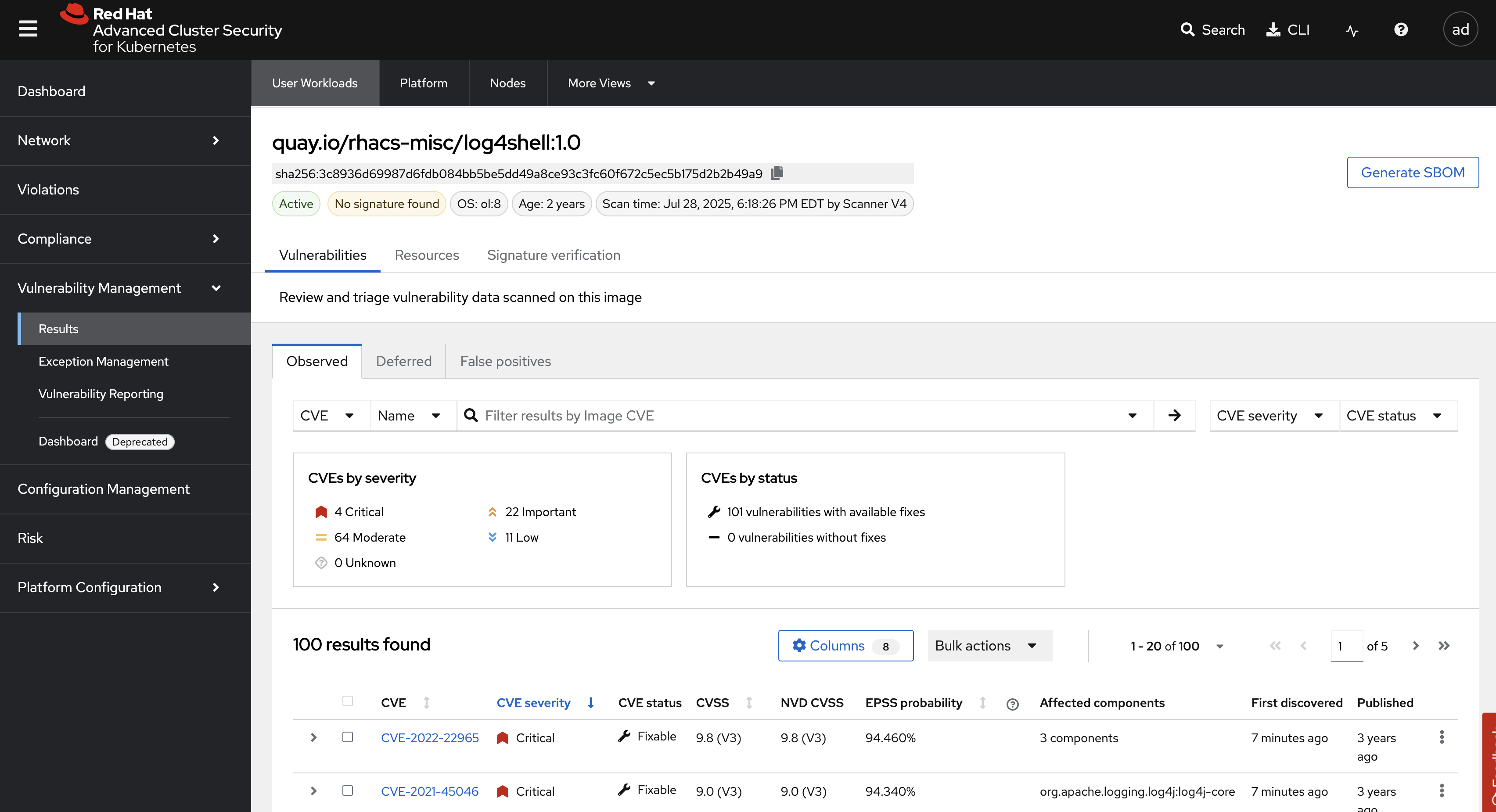
Scan the image to confirm the Log4Shell vulnerability is present:
roxctl --insecure-skip-tls-verify -e "$ROX_CENTRAL_ADDRESS:443" image scan --image=quay.io/rhacs-misc/log4shell:1.0 --force -o table --severity=CRITICALScan results for image: quay.io/rhacs-misc/log4shell:1.0
(TOTAL-COMPONENTS: 5, TOTAL-VULNERABILITIES: 4, LOW: 0, MODERATE: 0, IMPORTANT: 0, CRITICAL: 4)
+------------------------------------------------+---------+----------------+----------+------+---------------------------------------------------+---------------+----------+---------------+
| COMPONENT | VERSION | CVE | SEVERITY | CVSS | LINK | FIXED VERSION | ADVISORY | ADVISORY LINK |
+------------------------------------------------+---------+----------------+----------+------+---------------------------------------------------+---------------+----------+---------------+
| org.apache.logging.log4j:log4j-core | 2.14.1 | CVE-2021-44228 | CRITICAL | 10 | https://osv.dev/vulnerability/GHSA-jfh8-c2jp-5v3q | 2.15.0 | - | - |
| | +----------------+----------+------+---------------------------------------------------+---------------+----------+---------------+
| | | CVE-2021-45
.
.
.
WARN: A total of 4 unique vulnerabilities were found in 5 componentsLook for CVE-2021-44228 in the output. It should be at the top of the list.
4. Review the Vulnerability in the RHACS Console
Quickly identifying a vulnerability with RHACS enables you to proactively protect your workloads, minimize risk, and respond to security threats before they can be exploited.
-
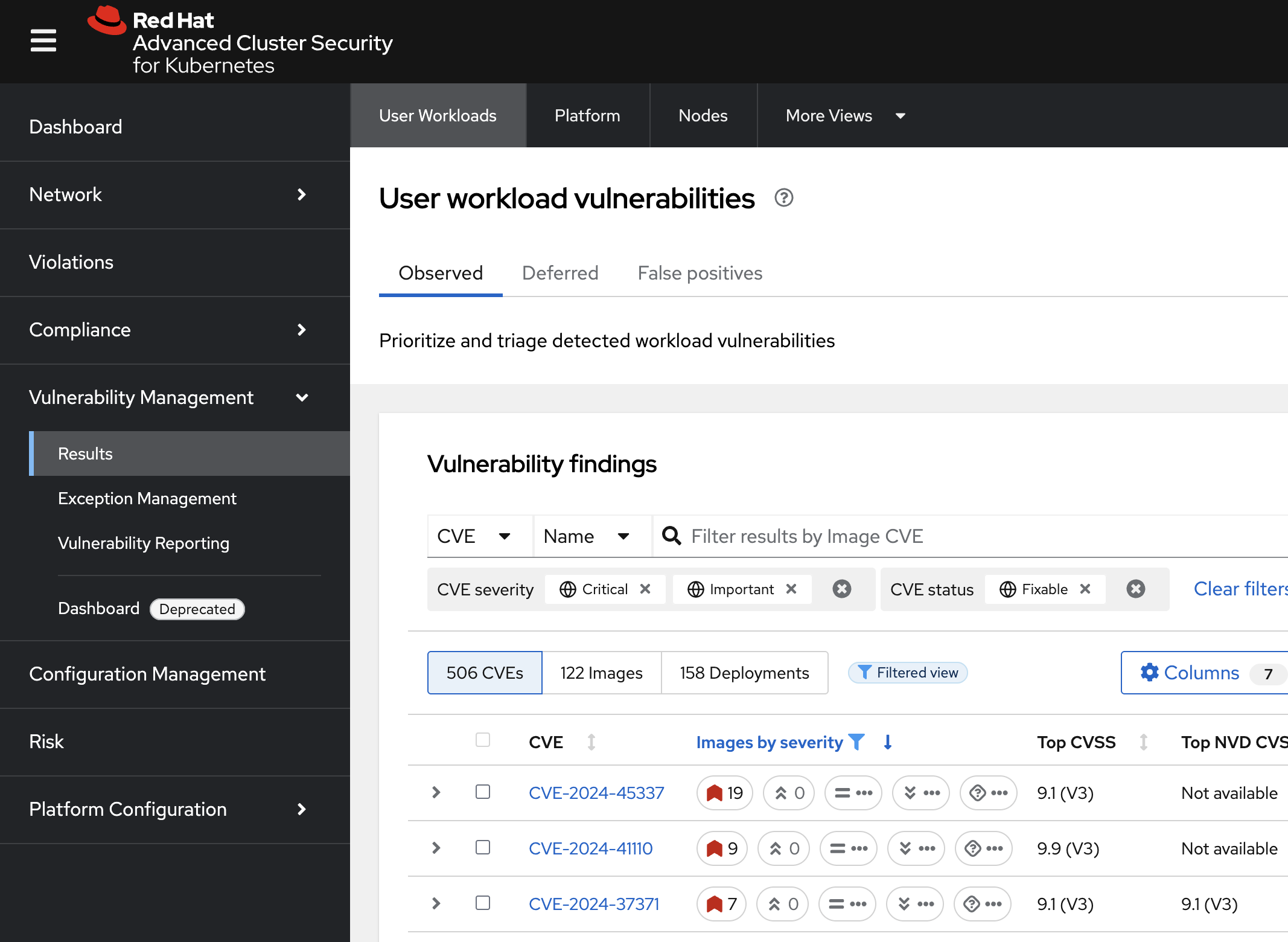
In the RHACS console, go to the Results page under the vulnerability management tab.
-
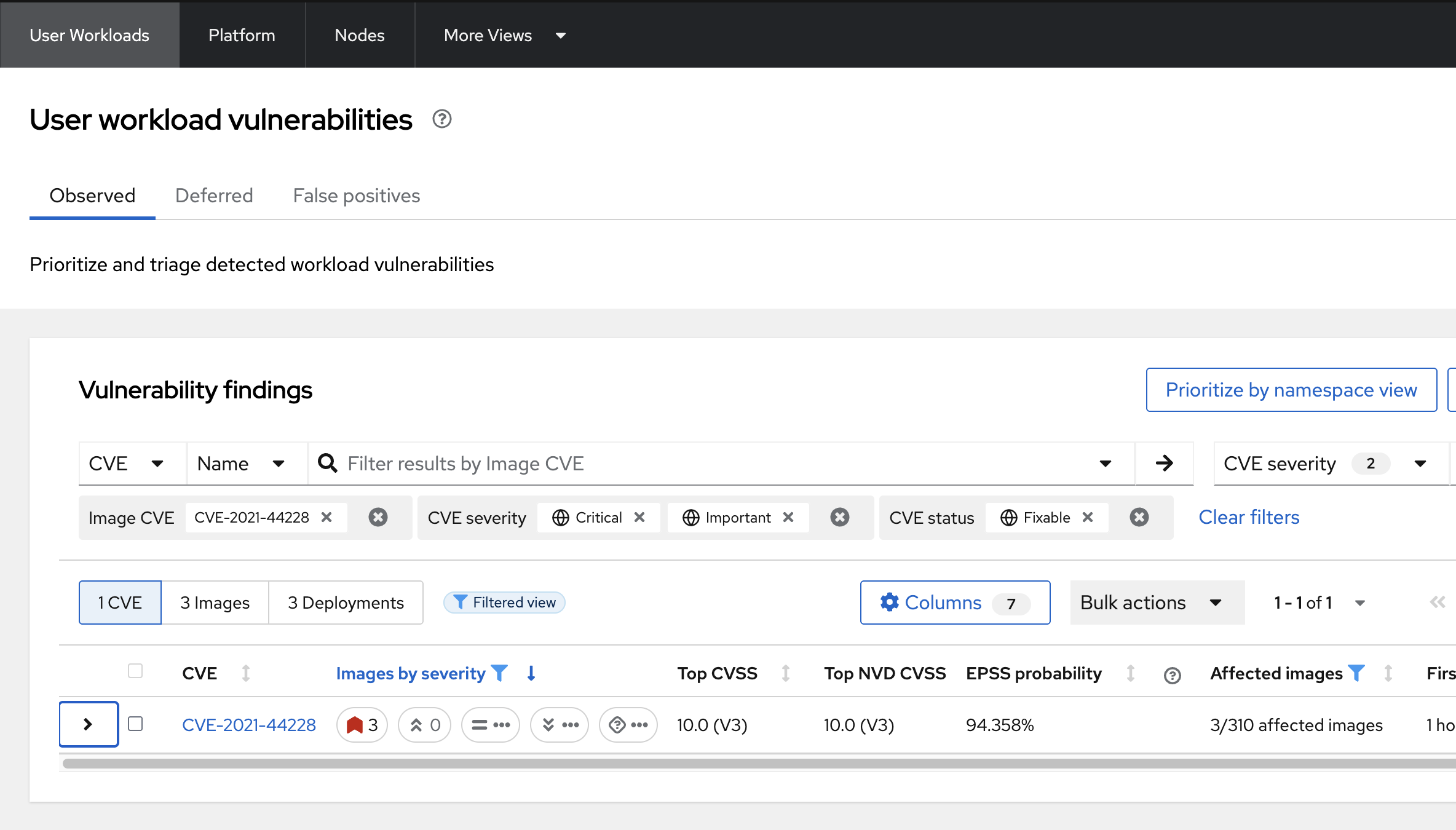
Filter for the Log4Shell CVE (CVE-2021-44228).
-
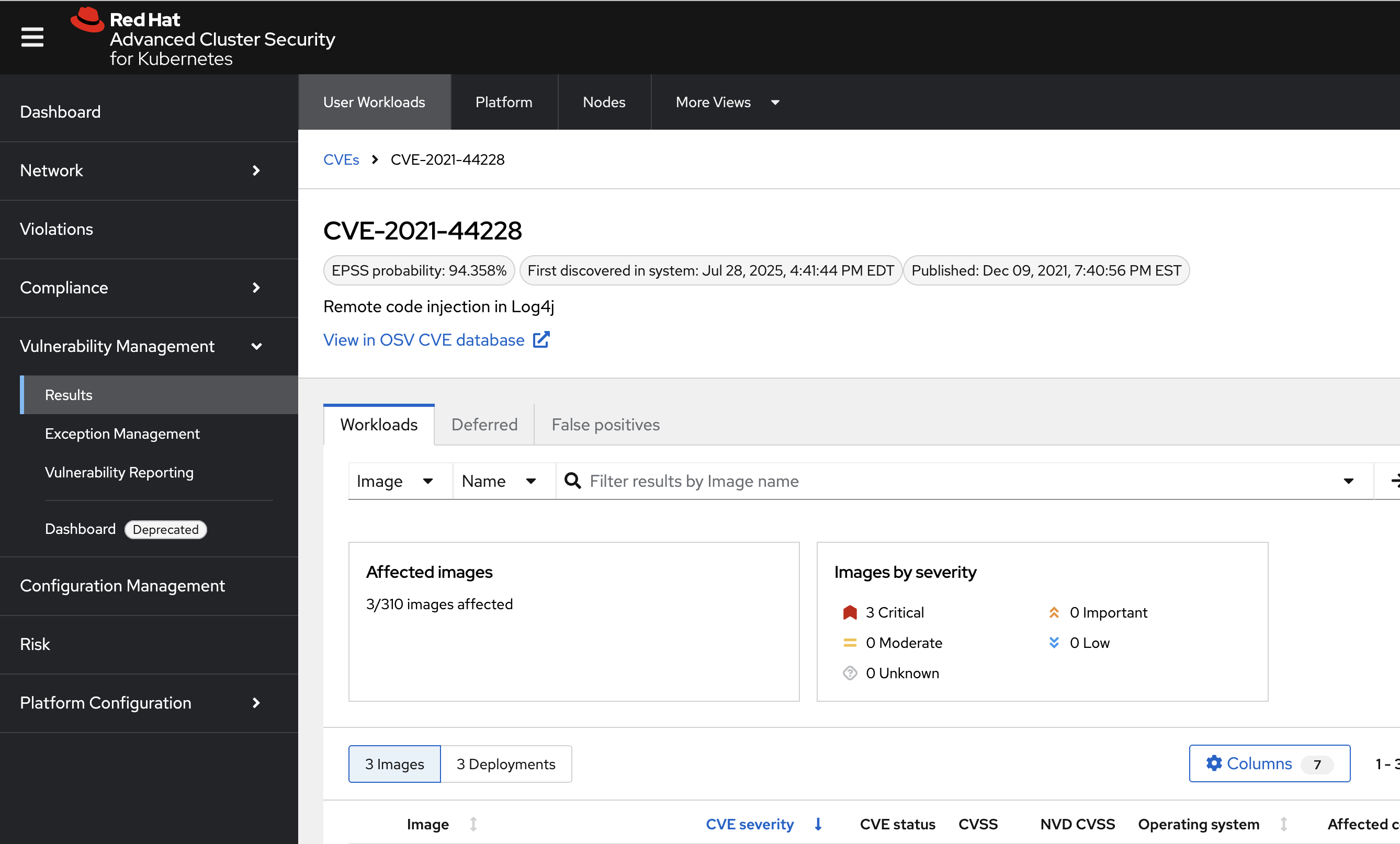
Click on the CVE-2021-44228 vulnerability to see the details.
-
Click on the quay.io/rhacs-misc/log4shell:1.0 tab to see the workload you deployed.
5. Apply Policy to Block Log4Shell at the build, deploy and runtime stages
Below, you will be deploying one policy that will block the log4shell vulnerability.
This policy blocks images containing the vulnerable Log4j version at build, deploy, and runtime. Execute the following commands to create the policy in the stackrox namespace:
cat <<EOF > block-log4shell-policy.yaml
apiVersion: config.stackrox.io/v1alpha1
kind: SecurityPolicy
metadata:
name: block-log4shell-cve-2021-44228
spec:
policyName: block-log4shell-cve-2021-44228
description: |
Blocks deployments containing the Log4Shell (CVE-2021-44228) vulnerability in Log4j.
This policy helps prevent exploitation of a critical remote code execution vulnerability
in affected versions of the Log4j library.
rationale: |
The Log4Shell vulnerability (CVE-2021-44228) is a critical security issue in the Log4j
library that allows remote code execution and has been widely exploited. Blocking deployments
with this vulnerability reduces the risk of compromise and lateral movement in your cluster.
remediation: |
Update your application dependencies to use Log4j version 2.15.0 or later, which contains
the fix for CVE-2021-44228. Rebuild and redeploy your application images after updating.
categories:
- Vulnerability Management
lifecycleStages:
- BUILD
- DEPLOY
eventSource: NOT_APPLICABLE
severity: CRITICAL_SEVERITY
enforcementActions:
- FAIL_BUILD_ENFORCEMENT
- SCALE_TO_ZERO_ENFORCEMENT
- UNSATISFIABLE_NODE_CONSTRAINT_ENFORCEMENT
policySections:
- sectionName: Rule 1
policyGroups:
- fieldName: CVE
booleanOperator: OR
values:
- value: CVE-2021-44228
criteriaLocked: false
mitreVectorsLocked: false
isDefault: false
EOF
oc apply -f block-log4shell-policy.yaml -n stackrox6. Review Violations
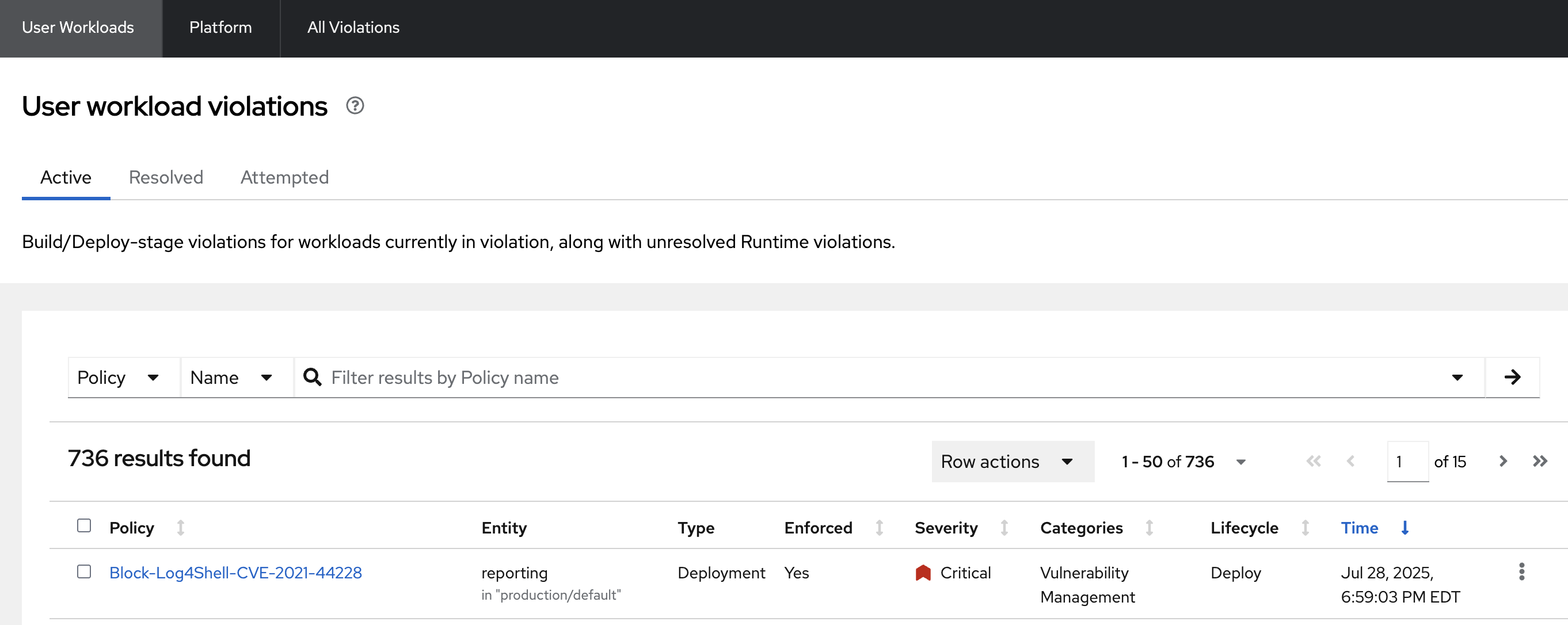
-
In the RHACS console, go to the Violations page.
-
You should see the log4shell policy at the top of the list.
Awesome! So we know you’ve "enforced" the policy. However, the workload is still running. This is because ACS will not kill a running workload to avoid disrupting the application.
oc get pods -l deployment=log4shell -n log4shellBut if you try to redeploy the application, you will see the following error:
oc create -f ~/deploy.yamlError from server (Failed currently enforced policies from RHACS): error when creating "/home/lab-user/deploy.yaml": admission webhook "policyeval.stackrox.io" denied the request:
The attempted operation violated 1 enforced policy, described below:
Policy: block-log4shell-cve-2021-44228
- Description:
↳ Blocks deployments containing the Log4Shell (CVE-2021-44228) vulnerability in
Log4j.
This policy helps prevent exploitation of a critical remote code execution
vulnerability
in affected versions of the Log4j library.
- Rationale:
↳ The Log4Shell vulnerability (CVE-2021-44228) is a critical security issue in the
Log4j
library that allows remote code execution and has been widely exploited.
Blocking deployments
with this vulnerability reduces the risk of compromise and lateral movement in
your cluster.
- Remediation:
↳ Update your application dependencies to use Log4j version 2.15.0 or later, which
contains
the fix for CVE-2021-44228. Rebuild and redeploy your application images after
updating.
- Violations:
- CVE-2021-44228 (CVSS 10) (severity Critical) found in component 'org.apache.logging.log4j:log4j-core' (version 2.14.1) in container 'log4shell'
In case of emergency, add the annotation {"admission.stackrox.io/break-glass": "ticket-1234"} to your deployment with an updated ticket numberCongrats! Moving forward no applications will be able to deploy with the vulnerable Log4j version!
7. Clean Up
Before you go! please Run these commands to clean up:
oc delete project log4shell || true
rm -f ~/deploy.yaml
oc delete sp block-log4shell-cve-2021-44228 -n stackrox
# Remove non-default policies (including log4shell)
ROX_CENTRAL_ADDRESS=$(oc -n stackrox get route central -o jsonpath='{.spec.host}')
curl -k -H "Authorization: Bearer $ROX_API_TOKEN" "https://$ROX_CENTRAL_ADDRESS/v1/policies" | \
jq -r '.policies[] | select(.isDefault|not) | .id' | \
xargs -I{} curl -k -X DELETE -H "Authorization: Bearer $ROX_API_TOKEN" "https://$ROX_CENTRAL_ADDRESS/v1/policies/{}"Thanks! Enjoy Black Hat!